Researchers have disclosed particulars of a newly identified macOS variant of a malware implant produced by a Chinese espionage threat actor known to strike attack corporations throughout Asia.
Attributing the attacks to a team tracked as Storm Cloud, cybersecurity company Volexity characterized the new malware, dubbed Gimmick, a “attribute-rich, multi-system malware spouse and children that works by using public cloud hosting solutions (these as Google Generate) for command-and-handle (C2) channels.”
The cybersecurity agency reported it recovered the sample via memory investigation of a compromised MacBook Pro jogging macOS 11.6 (Huge Sur) as element of an intrusion campaign that took location in late 2021.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“Storm Cloud is an sophisticated and multipurpose menace actor, adapting its resource set to match distinct working methods made use of by its targets,” Volexity researchers Damien Cash, Steven Adair, and Thomas Lancaster explained in a report.
“They make use of developed-in working system utilities, open up-supply applications, and tailor made malware implants to reach their goals. Leveraging cloud platforms for C2, these types of as using Google Drive, improves the chance of working undetected by network monitoring options.”
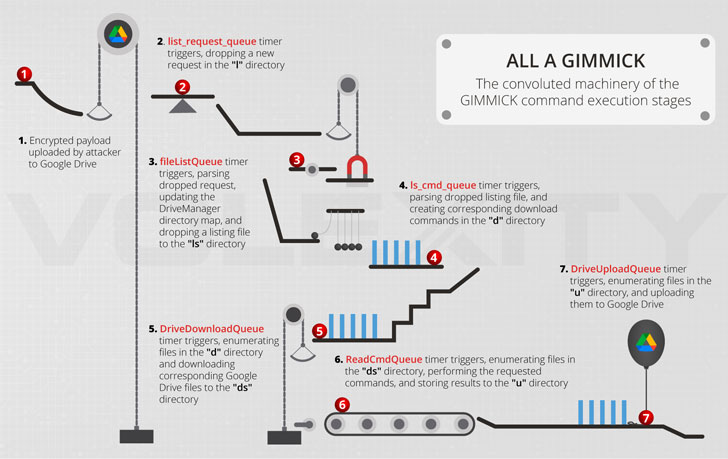
Unlike its Windows counterpart, which is coded in each .NET and Delphi, the macOS variation is penned in Goal C. The option of the programming languages apart, the two versions of the malware are regarded to share the similar C2 infrastructure and behavioral styles.
After deployed, Gimmick is launched possibly as a daemon or in the kind of a personalized software that is engineered to impersonate a plan frequently released by the focused consumer. The malware is configured to talk with its Google Drive-based C2 server only on functioning days in buy to more blend in with the network targeted visitors in the goal environment.
What is actually much more, the backdoor, other than retrieving arbitrary data files and executing instructions from the C2 server, arrives with its very own uninstall performance that makes it possible for it to erase itself from the compromised equipment.
To shield users in opposition to malware, Apple has issued new signatures to its developed-in anti-malware protection suite recognized as XProtect as of March 17, 2022 to block and remove the infections by means of its Malware Elimination Tool (MRT).
“The operate involved in porting this malware and adapting its techniques to a new operating system (macOS) is no mild undertaking and indicates the danger actor guiding it is nicely resourced, adept, and versatile,” the scientists claimed.
Identified this report interesting? Observe THN on Facebook, Twitter and LinkedIn to go through more distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com



 Over 200,000 MicroTik Routers Worldwide Are Under the Control of Botnet Malware
Over 200,000 MicroTik Routers Worldwide Are Under the Control of Botnet Malware