Microsoft on Wednesday drop mild on a earlier undocumented Mac trojan that it claimed has underwent numerous iterations given that its initial appearance in September 2020, effectively granting it an “growing development of subtle capabilities.”
The firm’s Microsoft 365 Defender Threat Intelligence Crew dubbed the new malware loved ones “UpdateAgent,” charting its evolution from a barebones details stealer to a 2nd-stage payload distributor as aspect of various attack waves noticed in 2021.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The latest marketing campaign saw the malware setting up the evasive and persistent Adload adware, but UpdateAgent’s potential to attain access to a gadget can theoretically be further more leveraged to fetch other, perhaps far more perilous payloads,” the scientists reported.
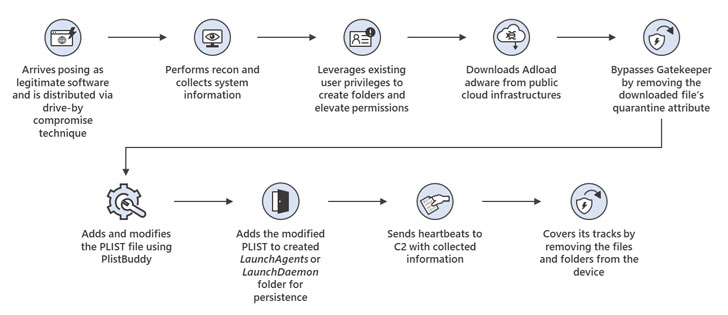
The actively in-enhancement malware is explained to be propagated through drive-by downloads or ad pop-ups that masquerade as respectable computer software like online video apps and help brokers, even as the authors have manufactured constant enhancements that have reworked UpdateAgent into a progressively persistent piece of malware.
Chief amid the advancements incorporate the capability to abuse existing user permissions to surreptitiously perform malicious pursuits and circumvent macOS Gatekeeper controls, a security element that guarantees only reliable programs from identified developers can be put in on a system.
In addition, UpdateAgent has been observed to just take advantage of public cloud infrastructure, specifically Amazon S3 and CloudFront expert services, to host its next-stage payloads, which includes adware, in the form of .DMG or .ZIP data files.
When installed, the Adload malware will make use of ad injection computer software and gentleman-in-the-middle (MitM) strategies to intercept and reroute users’ internet site visitors as a result of the attacker’s servers to insert rogue advertisements into web internet pages and research engine success to increase the possibilities of various bacterial infections on the equipment.
“UpdateAgent is uniquely characterized by its gradual upgrading of persistence tactics, a critical function that implies this trojan will likely proceed to use much more sophisticated methods in upcoming campaigns,” the scientists cautioned.
Uncovered this short article interesting? Follow THN on Facebook, Twitter and LinkedIn to read far more special written content we submit.
Some pieces of this post are sourced from:
thehackernews.com



 Cloudflare opens $3,000 bug bounty program to the public
Cloudflare opens $3,000 bug bounty program to the public