An not known menace actor has been noticed leveraging a destructive Windows kernel driver in attacks most likely concentrating on the Center East due to the fact at least May perhaps 2020.
Fortinet Fortiguard Labs, which dubbed the artifact WINTAPIX (WinTapix.sys), attributed the malware with lower self esteem to an Iranian danger actor.
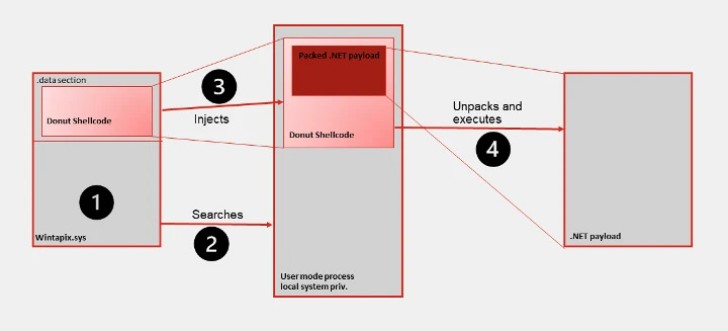
“WinTapix.sys is in essence a loader,” security researchers Geri Revay and Hossein Jazi mentioned in a report revealed on Monday. “As a result, its most important intent is to deliver and execute the next stage of the attack. This is accomplished employing a shellcode.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Samples and telemetry information analyzed by Fortinet show that the campaign’s most important concentrate is on Saudi Arabia, Jordan, Qatar, and the United Arab Emirates. The activity has not been tied to a identified threat actor or team.
By working with a malicious kernel mode driver, the idea is to subvert or disable security mechanisms and get entrenched entry to the qualified host.
This sort of motorists operate in just the kernel memory and can, therefore, execute any operation, such as altering critical security mechanisms and working arbitrary code with the best privileges.
In other words, it offers a stealthy way to infiltrate deeper into the targeted process, preserve persistence, and execute supplemental payloads or instructions as component of the threat actor’s multi-phase attack.
.jpg)
A critical security measure to mitigate against malicious motorists is Driver Signature Enforcement, which assures that only motorists signed by Microsoft can be loaded on the method. The tech huge also maintains driver block guidelines to safeguard in opposition to recognized susceptible motorists.
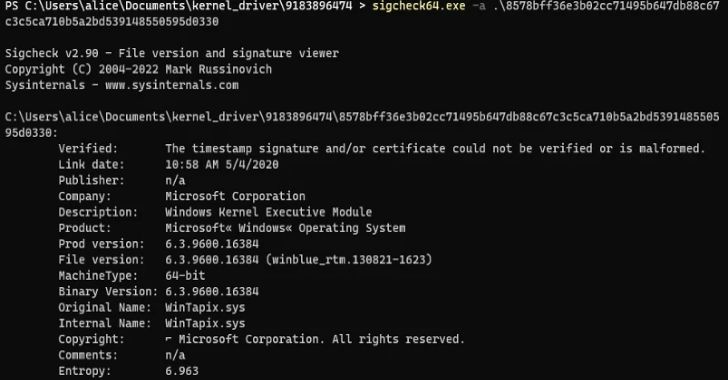
WinTapix.sys, on the other hand, will come with an invalid signature, indicating that the menace actor will have to first load a genuine but susceptible driver in purchase to launch WINTAPIX.
Upcoming WEBINARZero Have confidence in + Deception: Master How to Outsmart Attackers!
Uncover how Deception can detect highly developed threats, cease lateral motion, and greatly enhance your Zero Rely on technique. Sign up for our insightful webinar!
Save My Seat!
But at the time it is loaded in the kernel, WinTapix.sys is configured to inject an embedded shellcode into an ideal person manner method that, in turn, executes an encrypted .NET payload.
WINTAPIX, aside from embedding the shellcode made utilizing the open supply Donut job, establishes persistence by usually means of Windows Registry modifications that will allow it to be loaded even when the device is booted in Safe Method.
For its aspect, the .NET malware is equipped with backdoor and proxy functions to execute instructions, have out file download and upload, and operate as a proxy to move information in between two interaction endpoints.
“Because Iranian risk actors are recognised to exploit Trade servers to deploy further malware, it is also achievable that this driver has been employed alongside Trade attacks,” the researchers said.
“To that place, the compilation time of the motorists is also aligned with instances when Iranian danger actors had been exploiting Trade server vulnerabilities.”
The development will come as the ALPHV (aka BlackCat or Noberus) ransomware group has been noticed getting edge of a malicious signed driver to impair security defenses and escape detection for extended durations of time.
The driver in concern, ktgn.sys, is an updated edition of POORTRY which is signed applying a stolen or leaked cross-signing certificate, cybersecurity organization Pattern Micro explained in a report.
POORTRY is the identify assigned to a Windows kernel driver that arrives with capabilities to terminate security software package. Late very last calendar year, it was disclosed as utilised by ransomware gangs and a risk actor identified as UNC3944 (aka Roasted 0ktapus and Scattered Spider).
“Destructive actors that are actively in search of significant-privilege entry to the Windows running program use tactics that try to battle the enhanced protection on end users and procedures by using endpoint security system (EPP) and endpoint detection and reaction (EDR) systems,” Craze Micro reported.
“These malicious actors also are inclined to possess adequate money sources to either order rootkits from underground sources or to acquire code-signing certificates to build a rootkit.”
Discovered this post fascinating? Follow us on Twitter and LinkedIn to browse more exclusive content we publish.
Some sections of this article are sourced from:
thehackernews.com

 Two-Thirds of IT Leaders Say GDPR Has Reduced Consumer Trust
Two-Thirds of IT Leaders Say GDPR Has Reduced Consumer Trust