A novel credential-stealing malware termed Zaraza bot is staying supplied for sale on Telegram whilst also applying the well-known messaging company as a command-and-manage (C2).
“Zaraza bot targets a substantial variety of web browsers and is remaining actively distributed on a Russian Telegram hacker channel common with menace actors,” cybersecurity corporation Uptycs said in a report revealed past week.
“After the malware infects a victim’s laptop, it retrieves delicate data and sends it to a Telegram server where the attackers can obtain it instantly.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
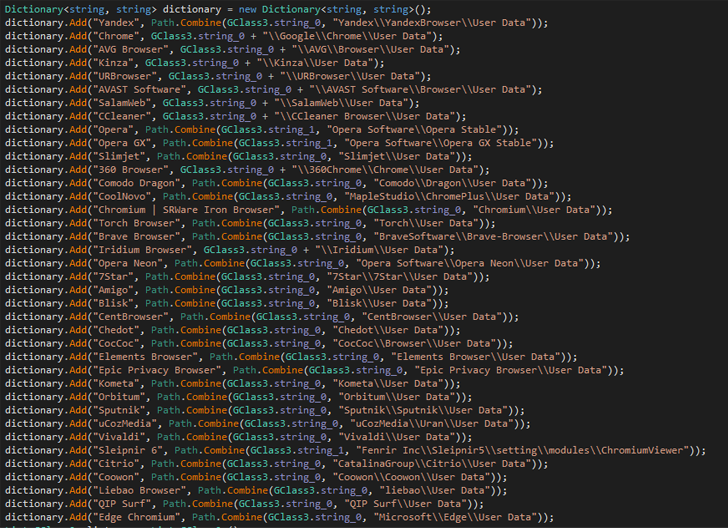
A 64-bit binary file compiled making use of C#, Zaraza bot is made to focus on as quite a few as 38 unique web browsers, like Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, Vivaldi, and Yandex. It is also geared up to seize screenshots of the lively window.
It can be the most recent illustration of malware which is able of capturing login credentials associated with on the web bank accounts, cryptocurrency wallets, email accounts, and other websites considered of value to the operators.
Stolen qualifications pose a severe risk as they not only allow for threat actors to attain unauthorized entry to victims’ accounts, but also conduct id theft and monetary fraud.
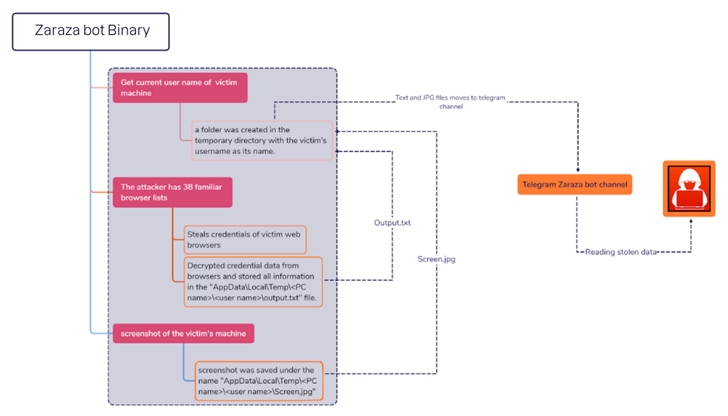
Evidence collected by Uptycs factors to Zaraza bot becoming provided as a business device for other cybercriminals for a subscription. It is really at the moment not clear how the malware is propagated, but details stealers have usually leveraged several methods these as malvertising and social engineering in the past.
The conclusions appear as eSentire’s Threat Response Unit (TRU) disclosed a GuLoader (aka CloudEyE) marketing campaign concentrating on the financial sector by way of phishing e-mail by using tax-themed lures to provide data stealers and distant obtain trojans (RATs) like Remcos RAT.
Future WEBINARMaster the Art of Dark Web Intelligence Gathering
Understand the artwork of extracting threat intelligence from the dark web – Be part of this specialist-led webinar!
Help you save My Seat!
The growth also follows a spike in malvertising and search engine poisoning methods to distribute a expanding number of malware family members by enticing users exploring for authentic purposes into downloading bogus installers containing stealer payloads.
Russian cybersecurity business Kaspersky, in a new assessment, revealed the use of trojanized cracked software program downloaded from BitTorrent or OneDrive to deploy CueMiner, a .NET-based mostly downloader that functions as a conduit to installer a cryptocurrency miner acknowledged as SilentCryptoMiner.
To mitigate risks stemming from stealer malware, it is really encouraged that customers help two-factor authentication (2FA) and apply program and running systems updates as and when they turn into obtainable.
Found this article attention-grabbing? Comply with us on Twitter and LinkedIn to examine much more exceptional material we submit.
Some components of this write-up are sourced from:
thehackernews.com


 Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability