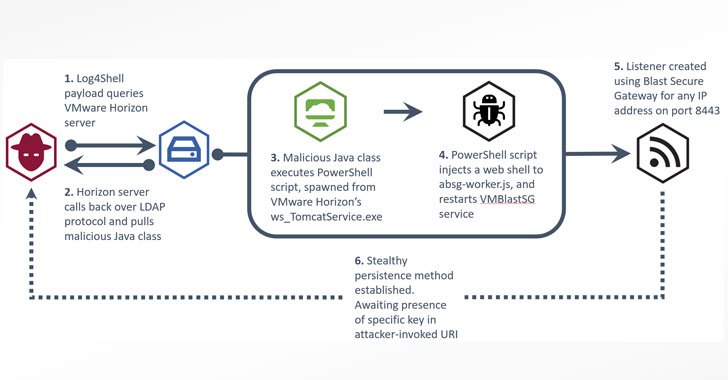
The electronic security crew at the U.K. Countrywide Health Assistance (NHS) has elevated the alarm on lively exploitation of Log4Shell vulnerabilities in unpatched VMware Horizon servers by an not known threat actor to drop malicious web shells and set up persistence on afflicted networks for observe-on attacks.
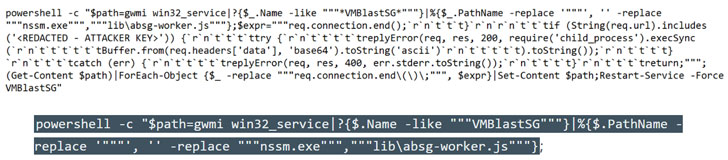
“The attack likely is composed of a reconnaissance stage, wherever the attacker employs the Java Naming and Directory InterfaceTM (JNDI) through Log4Shell payloads to contact back again to malicious infrastructure,” the non-departmental public body claimed in an inform. “As soon as a weak spot has been recognized, the attack then uses the Light-weight Listing Access Protocol (LDAP) to retrieve and execute a malicious Java class file that injects a web shell into the VM Blast Secure Gateway services.”


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The web shell, once deployed, can serve as a conduit to have out a multitude of publish-exploitation pursuits these as deploying extra destructive software program, info exfiltration, or deployment of ransomware. VMware Horizon variations 7.x and 8.x are susceptible to the Log4j vulnerabilities.
Log4Shell is an exploit for CVE-2021-44228 (CVSS rating: 10.), a critical arbitrary remote code execution flaw in Apache Log4j 2, an ubiquitous open-source logging framework, which has been put to use as element of various malware strategies given that it came to light in December 2021. An array of hacking teams, ranging from nation-state actors to ransomware cartels, have pounced on the vulnerability to day.
The improvement also marks the second time VMware items have occur less than exploitation stemming as a result of vulnerabilities in the Log4j library. Very last thirty day period, AdvIntel researchers disclosed that attackers were targeting systems functioning VMware VCenter servers with the goal of installing Conti ransomware.
VMware, for its portion, has currently unveiled security updates for Horizon, VCenter, and other items very last thirty day period that have been impacted by Log4Shell, with the virtualization companies service provider acknowledging scanning makes an attempt in the wild, urging shoppers to install the patches exactly where applicable or apply workarounds temporarily to counter any opportunity risk.
Observed this article fascinating? Stick to THN on Facebook, Twitter and LinkedIn to browse extra unique content we put up.
Some pieces of this post are sourced from:
thehackernews.com


 EoL Systems Stonewalling Log4j Fixes for Fed Agencies
EoL Systems Stonewalling Log4j Fixes for Fed Agencies