The North Korean state-backed hacking crew, if not recognized as the Lazarus Group, has been attributed to still yet another financially inspired campaign that leverages a trojanized decentralized finance (DeFi) wallet application to distribute a absolutely-showcased backdoor onto compromised Windows methods.
The app, which is outfitted with functionalities to preserve and deal with a cryptocurrency wallet, is also developed to trigger the launch of the implant that can take management of the infected host. Russian cybersecurity firm Kaspersky explained it to start with encountered the rogue application in mid-December 2021.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
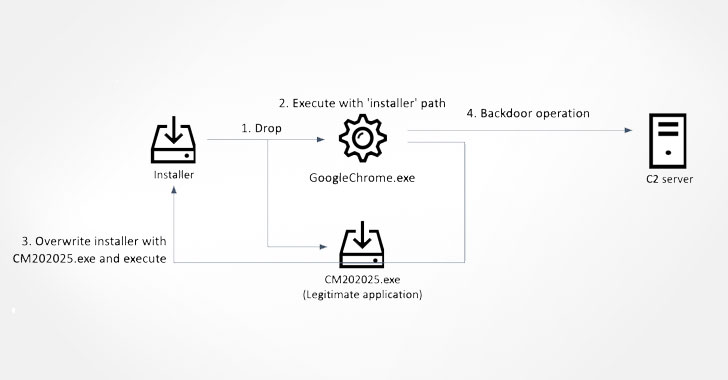
The infection plan initiated by the application also success in the deployment of the installer for a legitimate software, which receives overwritten with a trojanized variation in an exertion to deal with its tracks. That claimed, the original entry avenue is unclear, whilst it really is suspected to be a situation of social engineering.
The spawned malware, which masquerades as Google’s Chrome web browser, subsequently launches a wallet app crafted for the DeFiChain, although also setting up connections to a distant attacker-managed domain and awaiting even more recommendations from the server.
Primarily based on the response received from the command-and-command (C2) server, the trojan proceeds to execute a extensive assortment of commands, granting it the potential to acquire system information, enumerate and terminate processes, delete documents, launch new processes, and save arbitrary information on the machine.
The C2 infrastructure utilized in this marketing campaign exclusively consisted of earlier compromised web servers found in South Korea, prompting the cybersecurity enterprise to operate with the country’s computer crisis reaction crew (KrCERT) to dismantle the servers.
The findings occur much more than two months following Kaspersky disclosed details of a related “SnatchCrypto” campaign mounted by the Lazarus sub-group tracked as BlueNoroff to drain digital money from victims’ MetaMask wallets.
“For the Lazarus menace actor, financial achieve is one particular of the key motivations, with a distinct emphasis on the cryptocurrency business enterprise. As the value of cryptocurrency surges, and the attractiveness of non-fungible token (NFT) and decentralized finance (DeFi) businesses proceeds to swell, the Lazarus group’s focusing on of the financial marketplace keeps evolving,” Kaspersky Great scientists pointed out.
Found this posting interesting? Comply with THN on Facebook, Twitter and LinkedIn to read extra exclusive content material we publish.
Some elements of this post are sourced from:
thehackernews.com


 UK Spy Chief Hails Government Cell Tackling Kremlin Fake News
UK Spy Chief Hails Government Cell Tackling Kremlin Fake News