A cyberespionage group with ties to North Korea has resurfaced with a stealthier variant of its distant accessibility trojan called Konni to attack political institutions found in Russia and South Korea.
“The authors are regularly producing code improvements,” Malwarebytes researcher Roberto Santos mentioned. “Their endeavours are aimed at breaking the regular move recorded by sandboxes and generating detection harder, especially through typical signatures as critical areas of the executable are now encrypted.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Most the latest intrusions staged by the team, thought to be running below the Kimsuky umbrella, included focusing on the Russian Federation’s Ministry of International Affairs (MID) with New 12 months lures to compromise Windows systems with malware.
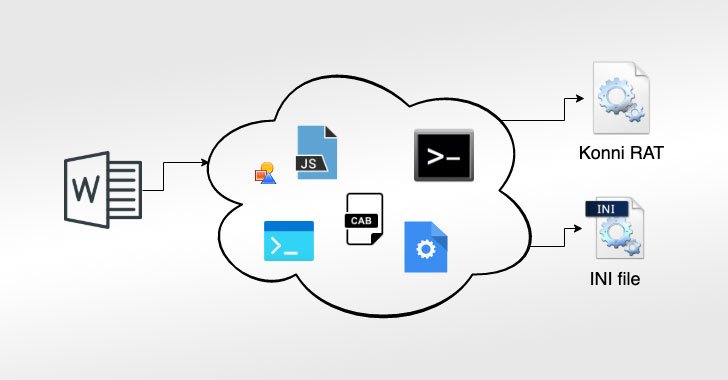
The infections, as with other attacks of this kind, starts with a malicious Microsoft Office environment document that, when opened, initiates a mult-stage approach that requires various shifting parts that help the attackers elevate privileges, evade detection, and ultimately deploy the Konni RAT payload on compromised techniques.
A new addition to the backdoor’s present capabilities is the transition from Foundation64 encoding to AES encryption to secure its strings and for obfuscating their legitimate function. On top of that, the a variety of guidance documents dropped to aid the compromise are also now encrypted employing AES.
“Cleverly, they reused the algorithm employed for string protection, earning the file layout similar to the protected strings layout, as they appear in raw memory,” Santox thorough.
The substantial updates are an example of how swiftly sophisticated actors can evolve their strategies and tactics to create one thing strong and powerful that can go previous security and detection layers.
Identified this article intriguing? Observe THN on Facebook, Twitter and LinkedIn to study additional distinctive content we write-up.
Some sections of this short article are sourced from:
thehackernews.com



 Podcast transcript: Inside the DDoS arms race
Podcast transcript: Inside the DDoS arms race