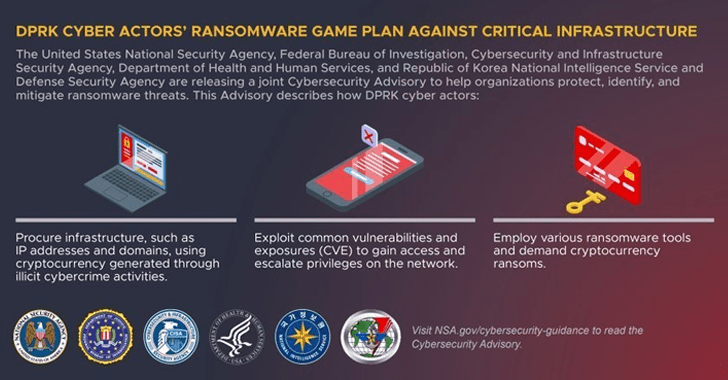
Point out-backed hackers from North Korea are conducting ransomware attacks versus health care and critical infrastructure services to fund illicit things to do, U.S. and South Korean cybersecurity and intelligence companies warned in a joint advisory.
The attacks, which need cryptocurrency ransoms in exchange for recovering obtain to encrypted documents, are created to help North Korea’s countrywide-amount priorities and aims.
This incorporates “cyber functions concentrating on the United States and South Korea governments — particular targets involve Section of Defense Information Networks and Defense Industrial Foundation member networks,” the authorities mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Threat actors with North Korea have been linked to espionage, economic theft, and cryptojacking functions for decades, which include the infamous WannaCry ransomware attacks of 2017 that infected hundreds of thousands of devices located in in excess of 150 nations around the world.
Considering that then, North Korean country-state crews have dabbled in multiple ransomware strains these types of as VHD, Maui, and H0lyGh0st to crank out a continuous stream of illegal revenues for the sanctions-hit routine.
Other than procuring its infrastructure as a result of cryptocurrency produced via its felony pursuits, the adversary is regarded to operate below 3rd-party foreign affiliate identities to conceal their involvement.
Attack chains mounted by the hacking crew entail the exploitation of known security flaws in Apache Log4j, SonicWall, and TerraMaster NAS appliances (e.g., CVE 2021-44228, CVE-2021-20038, and CVE-2022-24990) to obtain first obtain, pursuing it up by reconnaissance, lateral movement, and ransomware deployment.
In addition to applying privately made ransomware, the actors have been observed leveraging off-the-shelf equipment like BitLocker, DeadBolt, ech0raix, Jigsaw, and YourRansom for encrypting data files, not to point out even impersonating other ransomware teams such as REvil.
As mitigations, the agencies advocate companies to apply the theory of the very least privilege, disable needless network system administration interfaces, implement multi-layer network segmentation, need phishing-resistant authentication controls, and retain periodic info backups.
The notify comes as a new report from the United Nations located that North Korean hackers stole document-breaking virtual belongings estimated to be truly worth between $630 million and additional than $1 billion in 2022.
The report, seen by the Related Press, claimed the risk actors made use of more and more subtle approaches to achieve accessibility to digital networks concerned in cyberfinance, and to steal info from governments, firms, and persons that could be handy in North Korea’s nuclear and ballistic missile courses.
It further more termed out Kimsuky, Lazarus Team, and Andariel, which are all portion of the Reconnaissance General Bureau (RGB), for continuing to focus on victims with the purpose of making revenue and soliciting information and facts of worth to the hermit kingdom.
Discovered this write-up appealing? Stick to us on Twitter and LinkedIn to study additional unique written content we post.
Some elements of this article are sourced from:
thehackernews.com

 The IT Pro Podcast: Uprooting legacy tech
The IT Pro Podcast: Uprooting legacy tech