Threat actors these kinds of as the infamous Lazarus team are continuing to tap into the ongoing COVID-19 vaccine study to steal delicate information to speed up their countries’ vaccine-growth endeavours.
Cybersecurity business Kaspersky in-depth two incidents at a pharmaceutical firm and a governing administration ministry in September and Oct leveraging distinctive applications and techniques but exhibiting similarities in the post-exploitation approach, foremost the researchers to hook up the two attacks to the North Korean govt-linked hackers.
“These two incidents expose the Lazarus group’s curiosity in intelligence linked to COVID-19,” Seongsu Park, a senior security researcher at Kaspersky, explained. “Even though the group is mainly acknowledged for its economic actions, it is a very good reminder that it can go immediately after strategic investigate as nicely.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Kaspersky did not title the targeted entities but said the pharmaceutical company was breached on September 25, 2020, with the attack in opposition to the governing administration well being ministry happening a month later, on October 27.
Notably, the incident at the pharmaceutical firm — which is involved in building and distributing a COVID-19 vaccine — noticed the Lazarus group deploying the “BookCodes” malware, a short while ago used in a source-chain attack of a South Korean software package firm WIZVERA to set up remote administration resources (RATs) on goal units.
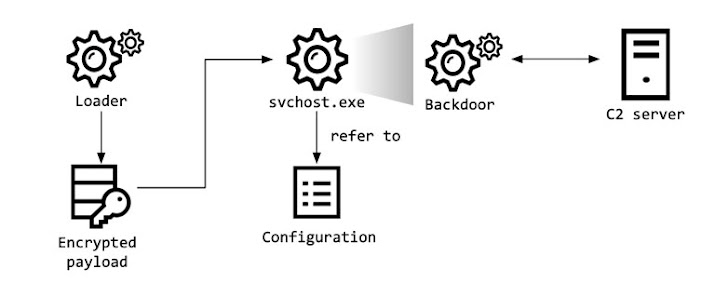
The preliminary entry vector utilized in the attack remains unknown as nonetheless, but a malware loader recognized by the researchers is explained to load the encrypted BookCodes RAT that comes with capabilities to accumulate method details, receive distant commands, and transmit the effects of the execution to command-and-handle (C2) servers located in South Korea.
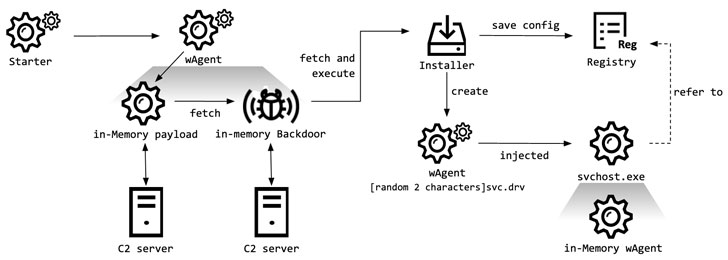
In a individual campaign aimed at the well being ministry, the hackers compromised two Windows servers to put in a malware recognized as “wAgent,” and then applied it to retrieve other malicious payloads from an attacker-managed server.
As with the earlier scenario, the researchers claimed they were unable to locate the starter module applied in the attack but suspect it to have a “trivial purpose” of managing the malware with precise parameters, adhering to which wAgent hundreds a Windows DLL that contains backdoor functionalities straight into memory.
“Making use of this in-memory backdoor, the malware operator executed various shell commands to gather victim details,” Park said.
Irrespective of the two malware clusters employed in the attacks, Kaspersky reported the wAgent malware utilized in October shared the similar an infection plan as the malware that the Lazarus team utilised formerly in attacks on cryptocurrency companies, citing overlaps in the malware naming scheme and debugging messages, and the use of Security Aid Provider as a persistence mechanism.
The growth is the hottest in a extended checklist of attacks capitalizing on the coronavirus pandemic — a pattern noticed in different phishing lures and malware strategies throughout the very last year. North Korean hackers are alleged to have qualified pharma companies in India, France, Canada, and the UK-dependent AstraZeneca.
Observed this posting intriguing? Comply with THN on Fb, Twitter and LinkedIn to examine extra distinctive written content we write-up.
Some areas of this article are sourced from:
thehackernews.com


 Can SolarWinds survive? For breached companies it’s a long, painful road to restoring trust
Can SolarWinds survive? For breached companies it’s a long, painful road to restoring trust