The infamous Lazarus Team actor has been observed mounting a new marketing campaign that will make use of the Windows Update support to execute its malicious payload, growing the arsenal of living-off-the-land (LotL) methods leveraged by the APT group to additional its goals.
The Lazarus Team, also identified as APT38, Hidden Cobra, Whois Hacking Staff, and Zinc, is the moniker assigned to the North Korea-dependent country-condition hacking team that’s been lively considering that at minimum 2009. Very last calendar year, the risk actor was joined to an elaborate social engineering campaign focusing on security researchers.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The hottest spear-phishing attacks, which Malwarebytes detected on January 18, originate from weaponized paperwork with career-themed lures impersonating the American world wide security and aerospace business Lockheed Martin.
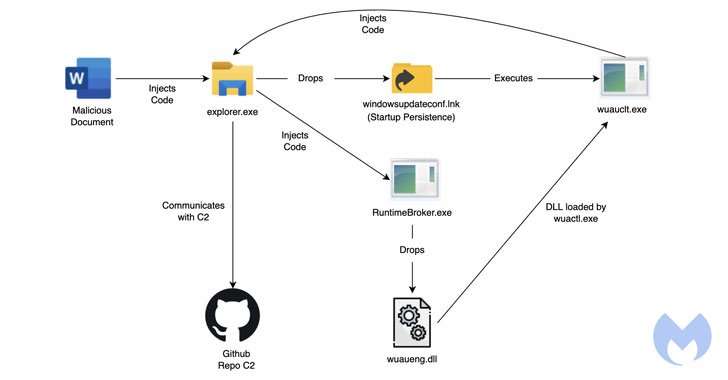
Opening the decoy Microsoft Term file triggers the execution of a destructive macro embedded within just the doc that, in switch, executes a Base64-decoded shellcode to inject a amount of malware parts into the explorer.exe course of action.
In the upcoming section, one of the loaded binaries, “drops_lnk.dll,” leverages the Windows Update client to operate a 2nd module termed “wuaueng.dll.” “This is an attention-grabbing approach employed by Lazarus to run its destructive DLL making use of the Windows Update Consumer to bypass security detection mechanisms,” scientists Ankur Saini and Hossein Jazi famous.
The cybersecurity agency characterized “wuaueng.dll” as “a person of the most crucial DLLs in the attack chain,” whose main objective is to build communications with a command-and-control (C2) server – a GitHub repository hosting malicious modules masquerading as PNG picture data files. The GitHub account is said to have been created on January 17, 2022.
Malwarebytes said that the one-way links to Lazarus Team are based on numerous pieces of proof tying them to earlier attacks by the exact same actor, such as infrastructure overlaps, doc metadata, and the use of position chances template to single out its victims.
“Lazarus APT is a person of the state-of-the-art APT groups that is acknowledged to target the defense sector,” the researchers concluded. “The team keeps updating its toolset to evade security mechanisms. Even nevertheless they have applied their previous job topic method, they used several new techniques to bypass detections.”
Identified this write-up interesting? Observe THN on Facebook, Twitter and LinkedIn to read through a lot more exceptional content material we post.
Some pieces of this posting are sourced from:
thehackernews.com


 North Korean Hackers Return with Stealthier Variant of KONNI RAT Malware
North Korean Hackers Return with Stealthier Variant of KONNI RAT Malware