A “extremely operational, destructive, and refined nation-condition activity team” with ties to North Korea has been weaponizing open source program in their social engineering strategies aimed at corporations around the globe considering the fact that June 2022.
Microsoft’s risk intelligence teams, alongside LinkedIn Threat Avoidance and Defense, attributed the intrusions with substantial self confidence to Zinc, which is also tracked less than the names Labyrinth Chollima.
Attacks specific staff in businesses throughout numerous industries, such as media, defense and aerospace, and IT providers in the U.S., the U.K., India, and Russia.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

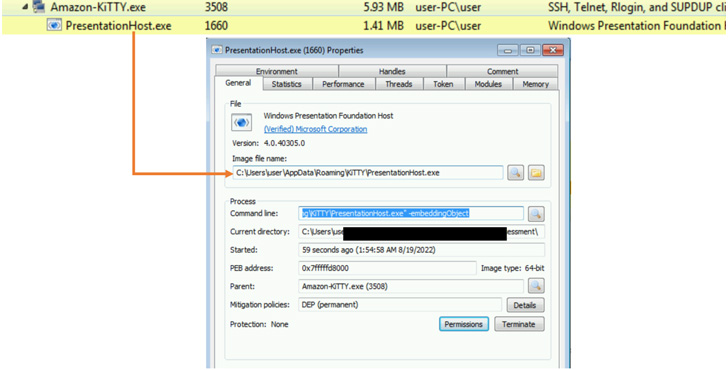
The tech big reported it observed Zinc leveraging a “vast vary of open-supply program together with PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software program installer for these attacks.”
According to CrowdStrike, Zinc “has been energetic given that 2009 in operations aimed at amassing political, armed forces, and financial intelligence on North Korea’s foreign adversaries and conducting currency era campaigns.”
The most current results dovetail with a current report from Google-owned Mandiant, which uncovered the adversary’s use of PuTTY by using fraudulent job lures shared with opportunity targets on LinkedIn as part of a campaign dubbed Procedure Aspiration Job.
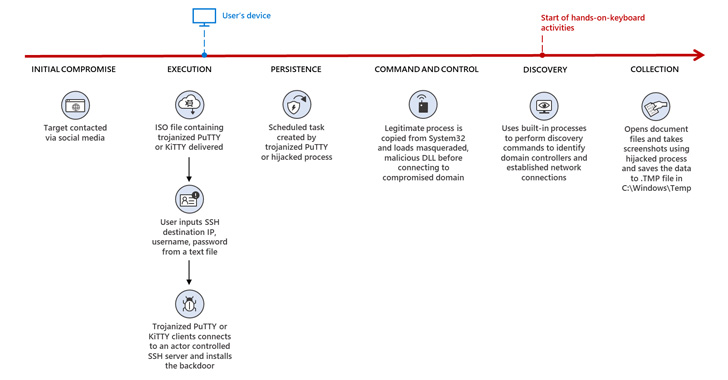
This consists of creating first connections with individuals by posing as recruitment industry experts as a have faith in-creating work out, in advance of relocating the conversation to WhatsApp, exactly where a tailor-made lure document or seemingly benign software is shared, correctly activating the infection sequence.
A effective compromise is adopted by the menace actor shifting laterally throughout the network and exfiltrating gathered information and facts of desire by deploying a backdoor named ZetaNile (aka BLINDINGCAN OR AIRDRY).

But in a bid to evade security defenses and keep away from boosting red flags, the implant is downloaded only when the sufferer employs the SSH purchasers to hook up to a certain IP tackle by way of the qualifications specified in a individual text file.
Furthermore, attacks utilizing the trojanized model of TightVNC Viewer are configured to put in the backdoor only when the consumer selects a individual remote host from the solutions supplied.
“Zinc attacks appear to be determined by standard cyberespionage, theft of personal and corporate facts, economical gain, and corporate network destruction,” the firm explained.
“Zinc attacks bear lots of hallmarks of condition-sponsored things to do, this kind of as heightened operational security, subtle malware that evolves about time, and politically inspired concentrating on.”
Identified this report intriguing? Comply with THN on Fb, Twitter and LinkedIn to go through far more unique articles we submit.
Some parts of this post are sourced from:
thehackernews.com

 GSMA partners with IBM, Vodafone on Post-Quantum Telco Network Taskforce
GSMA partners with IBM, Vodafone on Post-Quantum Telco Network Taskforce