A new cyber espionage team named Gelsemium has been connected to a source chain attack focusing on the NoxPlayer Android emulator that was disclosed before this yr.
The results arrive from a systematic evaluation of a number of campaigns carried out by the APT crew, with proof of the earliest attack relationship back again all the way to 2014 below the codename Procedure TooHash based mostly on malware payloads deployed in all those intrusions.
“Victims of these strategies are positioned in East Asia as perfectly as the Center East and include governments, religious organizations, electronics makers and universities,” cybersecurity business ESET stated in an evaluation released last week.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“Gelsemium’s whole chain might seem basic at initially sight, but the exhaustive configurations, implanted at each and every phase, modify on-the-fly options for the remaining payload, producing it tougher to fully grasp.”
Specific countries include things like China, Mongolia, North and South Korea, Japan, Turkey, Iran, Iraq, Saudi Arabia, Syria, and Egypt.
Because its origins in the mid-2010s, Gelsemium has been discovered employing a wide range of malware supply methods ranging from spear-phishing paperwork exploiting Microsoft Business vulnerabilities (CVE-2012-0158) and watering holes to a distant code execution flaw in Microsoft Trade Server — very likely CVE-2020-0688, which was tackled by the Windows maker in June 2020 — to deploy the China Chopper web shell.
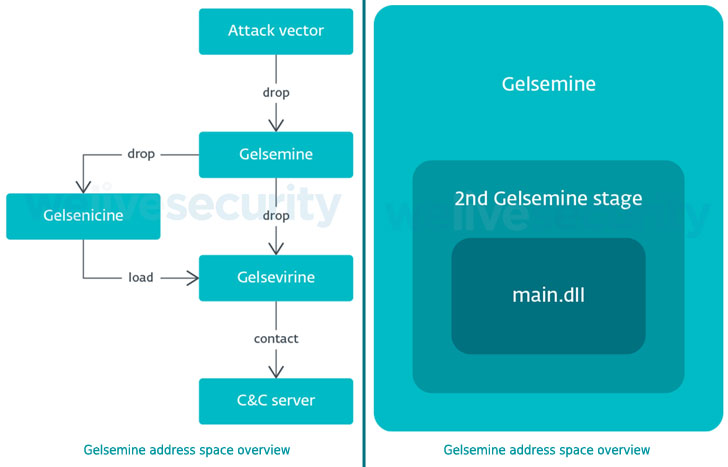
According to ESET, Gelsemium’s first stage is a C++ dropper named “Gelsemine,” which deploys a loader “Gelsenicine” onto the concentrate on technique, which, in switch, retrieves and executes the primary malware “Gelsevirine” which is capable of loading additional plug-ins supplied by the command-and-control (C2) server.
The adversary is stated to have been powering a provide chain attack aimed at BigNox’s NoxPlayer, in a campaign dubbed “Procedure NightScout,” in which the software’s update mechanism was compromised to set up backdoors these types of as Gh0st RAT and PoisonIvy RAT to spy on its victims, capture keystrokes, and collect precious information.

“Victims initially compromised by that source chain attack have been afterwards currently being compromised by Gelsemine,” ESET scientists Thomas Dupuy and Matthieu Faou famous, with similarities observed amongst the trojanized variations of NoxPlayer and Gelsemium malware.
What is actually more, a different backdoor termed Chrommme, which was detected on an unnamed organization’s machine also compromised by the Gelsemium group, made use of the identical C2 server as that of Gelsevirine, increasing the probability that the risk actor might be sharing the attack infrastructure across its malware toolset.
“The Gelsemium biome is extremely attention-grabbing: it exhibits several victims (according to our telemetry) with a wide selection of adaptable components,” the researchers concluded. “The plug-in program shows that builders have deep C++ know-how.”
Discovered this short article attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to go through much more distinctive content we submit.
Some parts of this short article are sourced from:
thehackernews.com


 Millions of Volkswagen customers affected by data breach
Millions of Volkswagen customers affected by data breach