A “logical flaw” has been disclosed in NPM, the default deal manager for the Node.js JavaScript runtime atmosphere, that allows malicious actors to pass off rogue libraries as authentic and trick unsuspecting developers into setting up them.
The supply chain threat has been dubbed “Package Planting” by researchers from cloud security firm Aqua. Pursuing responsible disclosure on February 10, the fundamental issue was remediated by NPM on April 26.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Up right until just lately, NPM authorized adding everyone as a maintainer of the package devoid of notifying these end users or obtaining their consent,” Aqua’s Yakir Kadkoda explained in a report released Tuesday.
This effectively meant that an adversary could develop malware-laced offers and assign them to dependable, well-liked maintainers without their know-how.
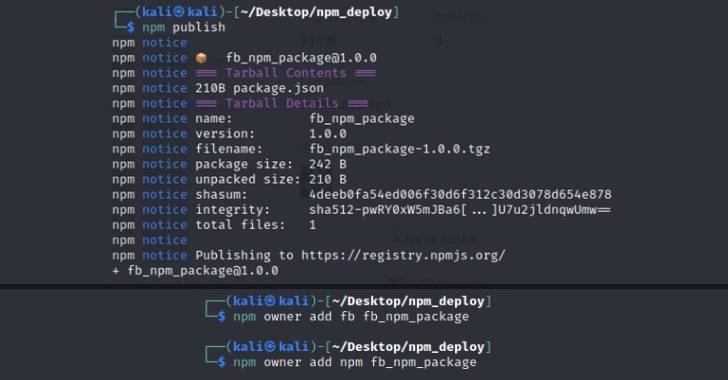
The idea here is to insert credible homeowners related with other preferred NPM libraries to the attacker-controlled poisoned offer in hopes that performing so would entice developers into downloading it.
The outcomes of these types of a source chain attack are significant for a range of good reasons. Not only does it give a fake sense of have faith in amongst developers, it could also inflict reputational damage to respectable deal maintainers.

The disclosure will come as Aqua uncovered two extra flaws in the NPM system similar to two-factor authentication (2FA) that could be abused to aid account takeover attacks and publish destructive deals.
“The main dilemma is that any npm user can carry out this and insert other NPM people as maintainers of their own package deal,” Kadkoda mentioned. “At some point, developers are responsible for what open resource deals they use when making applications.”
Discovered this posting fascinating? Follow THN on Facebook, Twitter and LinkedIn to read additional special written content we post.
Some parts of this write-up are sourced from:
thehackernews.com


 Microsoft Discovers New Privilege Escalation Flaws in Linux Operating System
Microsoft Discovers New Privilege Escalation Flaws in Linux Operating System