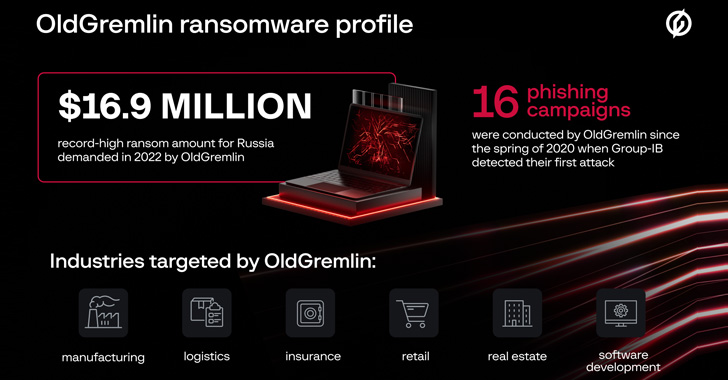
A Russian-talking ransomware team dubbed OldGremlin has been attributed to 16 destructive campaigns aimed at entities running in the transcontinental Eurasian country more than the training course of two and a 50 % several years.
“The group’s victims involve corporations in sectors these types of as logistics, sector, insurance coverage, retail, genuine estate, software progress, and banking,” Group-IB stated in an exhaustive report shared with The Hacker Information. “In 2020, the team even targeted an arms maker.”
In what is actually a rarity in the ransomware landscape, OldGremlin (aka TinyScouts) is a single of the very several financially enthusiastic cybercrime gangs that mostly focuses on Russian corporations.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Other noteworthy groups consist of Dharma, Crylock, and Thanos, contributing to an uptick in ransomware attacks concentrating on organizations in the region by more than 200% in 2021.
OldGremlin to start with came to mild in September 2020 when the Singapore-headquartered cybersecurity enterprise disclosed nine strategies orchestrated by the actor in between Might and August. The 1st attack was detected in early April 2020.
In all, the team is mentioned to have conducted 10 phishing email campaigns in 2020, adopted by a person hugely prosperous attack in 2021 and five extra in 2022, with ransom calls for touching a report $16.9 million.
“OldGremlin completely scientific tests their victims,” Group-IB defined. “The demanded ransom is hence frequently proportional to the company’s dimension and earnings and is clearly better than the budget important for ensuring a suited level of information and facts security.”

Recognised to primarily concentrate on business networks functioning on Windows, attacks mounted by OldGremlin have leveraged phishing email messages masquerading as tax and legal companies firms to dupe victims into clicking on fraudulent back links and downloading malicious files, letting the attackers to worm their way inside the networks.
“The threat actors often pose as perfectly-recognized corporations, which includes the media team RBC, the authorized assistance process Marketing consultant Additionally, the business 1C-Bitrix, the Russian Union of Industrialists and Entrepreneurs, and Minsk Tractor Operates,” Group-IB stated.
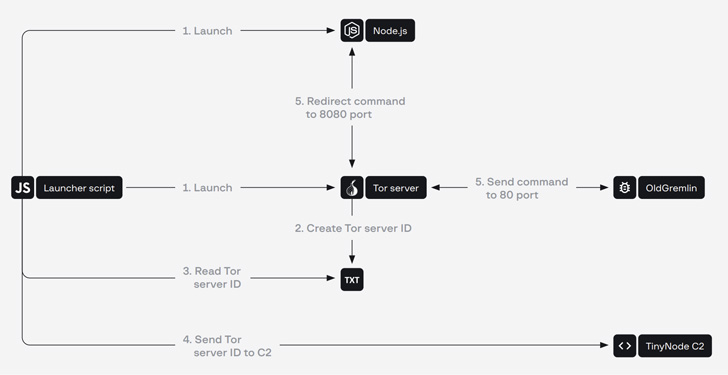
Upon getting an original foothold, OldGremlin moves to establish persistence by producing scheduled duties, gaining elevated privileges making use of Cobalt Stroke, and even flaw in Cisco AnyConnect (CVE-2020-3153 and CVE-2020-3433), while also getting distant access to the compromised infrastructure working with applications these as TeamViewer.
Some of the factors that make the crew stand out from other ransomware teams is that it will not depend on double extortion to coerce qualified companies into paying up even with exfiltrating the details. It has also been observed taking extended breaks following each individual effective attack.
What is actually more, the regular dwell time till ransomware deployment has been pegged at 49 times, nicely higher than the reported 11 day median dwell time, suggesting extended efforts on portion of the actor to analyze the breached domain (which is accomplished working with a resource known as TinyScout).

OldGremlin’s most the latest phishing wave occurred on August 23, 2022, with email messages embedding backlinks pointing to a ZIP archive payload hosted on Dropbox to activate the killchain.
These archive files, in turn, harbor a rogue LNK file (dubbed TinyLink) that downloads a backdoor referred to as TinyFluff, which is just one among the four implants made use of by the group: TinyPosh, TinyNode, and TinyShell, just before deleting information backups and dropping the .NET-centered TinyCrypt ransomware.
- TinyPosh: A PowerShell trojan engineered to gather and transfer delicate facts about the infected program to a remote server, and start supplemental PowerShell scripts.
- TinyNode: A backdoor that operates the Node.js interpreter to execute instructions obtained from a command-and-command (C2) server in excess of the Tor network.
- TinyFluff: A successor to TinyNode, which is made use of as the major downloader for getting and working destructive scripts.
Also set to use by OldGremlin are other tools this sort of as TinyShot, a console utility for capturing screenshots, TinyKiller, which kills antivirus processes by means of a deliver your have vulnerable driver (BYOVD) attack focusing on gdrv.sys and RTCore64.sys motorists.

It’s worthy of noting that the operators powering the BlackByte ransomware team ended up also lately observed leveraging the very same flaw in the RTCore64.sys driver to flip off security remedies in the hacked devices.
A person other unusual software used by OldGremlin in its attacks is a .NET console app known as TinyIsolator, which quickly cuts off the host from the network by disabling network adaptors prior to executing the ransomware.
On top rated of that, the group’s malware arsenal encompasses a Linux variation of TinyCrypt, which is penned in GO and introduced immediately after deleting .bash_background documents, modifying consumer passwords to restrict accessibility to the compromised host, and disabling SSH.
“OldGremlin has debunked the myth that ransomware groups are indifferent to Russian firms,” Ivan Pisarev, head of dynamic malware examination crew at Group-IB, claimed.
“Irrespective of the simple fact that OldGremlin has been focusing on Russia so considerably, they really should not be underestimated in other places. Lots of Russian-speaking gangs commenced off by concentrating on providers in publish-Soviet house and then switched to other geographies.”
Identified this article appealing? Follow THN on Fb, Twitter and LinkedIn to examine a lot more distinctive content we write-up.
Some components of this write-up are sourced from:
thehackernews.com

 FBI Warns Students Against Loan Forgiveness Scammers
FBI Warns Students Against Loan Forgiveness Scammers