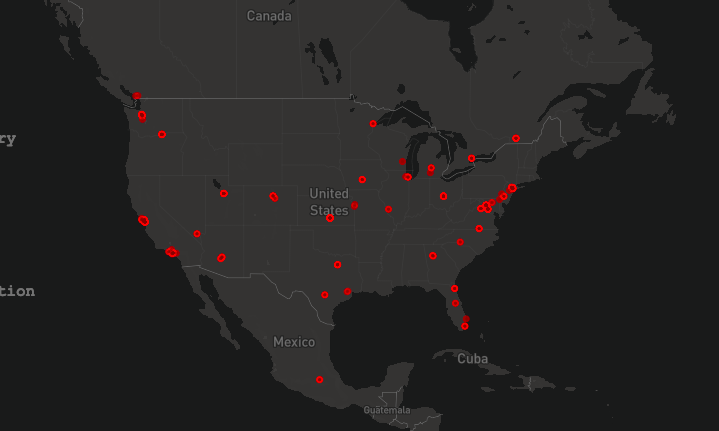
Seen in this article, Comparitech’s ransomware map
Human-powered gangs continue being the most hazardous and insidious threat on the ransomware entrance, but a recently introduced map element serves as a reminder that there is still a vast array of automatic strategies developed to serve up ransomware as perfectly.
Current on a each day foundation, the map, from Comparitech, visualizes attempted ransomware attacks around the entire world about the earlier a few weeks, demonstrating the geolocations of publicly available, compromised IPs functioning databases that have been served a ransomware file. The data isn’t especially actionable, but it does deliver a strong concept about the global scope of the ransomware trouble and sure general developments.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
For instance, over four months of aggregated knowledge, the normal bitcoin demanded from these automated attacks was .02, or $8,025.18 at the level of exchange as of June 14, and the ordinary deadline was 48 hours.
“The info is sourced via random port scanning and automated investigation of open ports working with API-streamed data coming from lookup engines these kinds of as Shodan, BinaryEdge, Censys and Zoomeye,” reported head of Comparitech’s cybersecurity exploration group Bob Diachenko. “We glimpse at the database banners that include the details we aggregate: IP, geographic locale, style of database and port. When we see an index or collection named ‘Readme’ and its permutations, we process its content material to extract the normal BTC demanded and the most usually employed email and wallet tackle.”
For illustration, Comparitech found just one Read_me note in an infected Elasticsearch cluster that warned the receiver to pay back .0175 bitcoins inside of 48 several hours to recover encrypted info. “After 48 hours expiration we will leaked and exposed [sic] all your details,” the be aware mentioned. “In scenario of refusal to shell out, we will get hold of the Basic Information Defense Regulation, GDPR and notify them that you retail store person data in an open up [forum] and is no[t] safe and sound.”
It is not clear what share of the whole automated ransomware attacks about the planet is represented by this map – nor is it specified if any of the brazenly accessible databases have been intentionally left open as a honeypot.
“Keeping in brain that this scan only addresses unprotected databases linked to the community internet as the attack vector, it is a practical visualization,” explained Dirk Schrader, worldwide vice president, security exploration at New Net Systems. “Displaying the distribute about the globe [and] the number of each day attacks tends to make it an impressive map for the uninformed and will help to increase awareness.”
Even now, “information security industry experts know that there are a lot more attack vectors for ransomware to have an eye on,” Schrader ongoing. “A nicely-ready firm will use out there sources like Shodan or Censys, furthermore [their] possess scanning abilities and gadget hardening and adjust handle [practices] to decrease its attack surface area.”
Other commentators, which includes Joseph Carson, main security scientist and advisory CISO at ThycoticCentrify, didn’t see significantly functional use for the map, even so.
“I did not come across it very… actionable, which is what I actually would like to see even so it was exciting to see where by the victims of ransomware attacks are located,” stated Carson. “While it is a terrific visualization, it [does] not aid encourage businesses executives to make investments in security to prevent them from getting the up coming victim.”
Yet, Diachenko reported Comparitech is presenting the device due to the fact “we required to spotlight the worth of pursuing the fundamental cyber cleanliness procedures and supply an even clearer photo of ransomware incidents across the world. In most circumstances organizations ignore them and imagine that ransomware gangs run mostly as condition-amount actors and focus on major and critical infrastructure objects. The reality is that there is a massive range of ransomware actors that simply scan and strike the uncovered databases with a ransom be aware hoping to get a thing.”
“There is no rapid action that can be taken right after wanting at the map,” he ongoing. “However, its major objective is to bring about the intention to test if your company’s security perimeter is risk-free now and do that ASAP.”
Some pieces of this short article are sourced from:
www.scmagazine.com

 ServiceNow partners with ZScaler for remote access security
ServiceNow partners with ZScaler for remote access security