A hacktivist collective called GhostSec has claimed credit for compromising as quite a few as 55 Berghof programmable logic controllers (PLCs) utilised by Israeli organizations as aspect of a “Cost-free Palestine” marketing campaign.
Industrial cybersecurity business OTORIO, which dug further into the incident, said the breach was produced achievable owing to the simple fact that the PLCs were obtainable by the Internet and had been secured by trivially guessable qualifications.
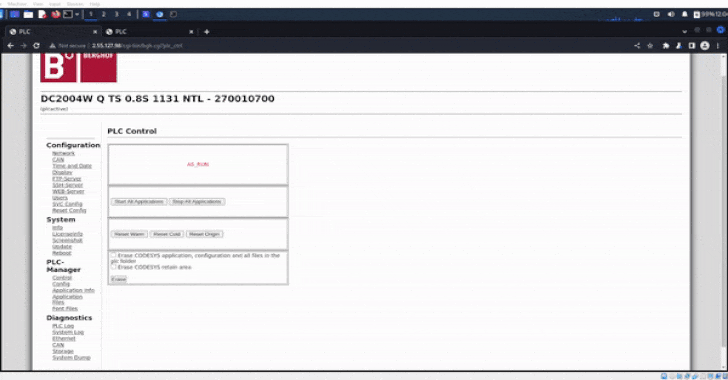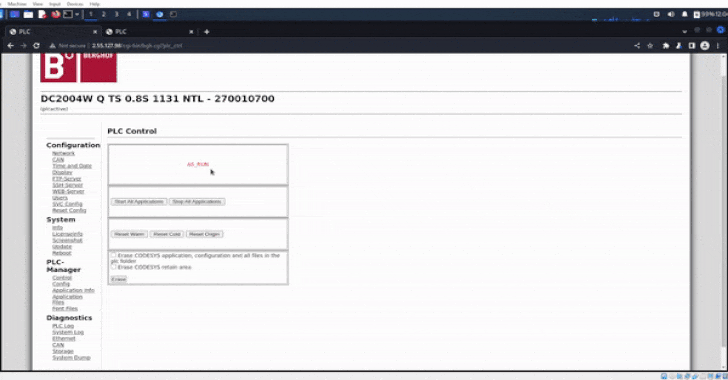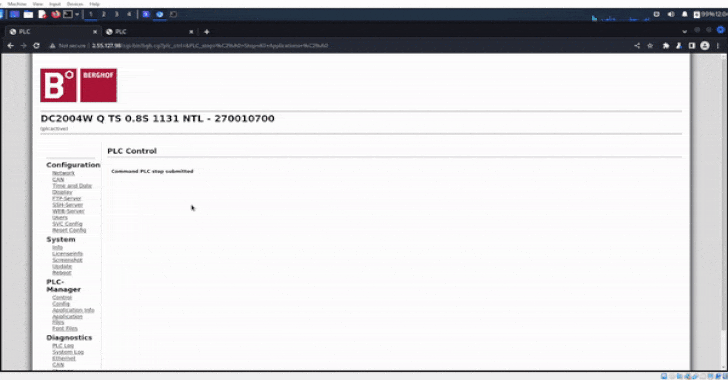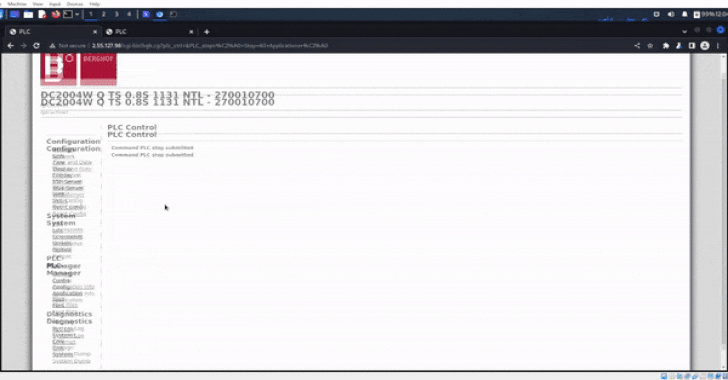
Information of the compromise first came to mild on September 4 after GhostSec shared a online video on its Telegram channel demonstrating a effective login to the PLC’s admin panel, in addition to dumping details from the hacked controllers.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Israeli business stated the method dumps and screenshots were exported specifically from the admin panel next unauthorized obtain to the controllers via their public IP addresses.

GhostSec (aka Ghost Security), first recognized in 2015, is a self-proclaimed vigilante group that was in the beginning shaped to focus on ISIS internet sites that preach Islamic extremism.
Earlier this February, the team rallied its guidance for Ukraine in the fast aftermath of Russia’s military invasion of the state. Considering the fact that late June, it has also participated in a marketing campaign concentrating on Israeli corporations and enterprises.
“The group pivoted from their typical operations and started to target many Israeli companies, presumably gaining access to several IoT interfaces and ICS/SCADA techniques, which led to doable disruptions,” Cyberint observed on July 14.
The attacks from Israeli targets, dubbed “#OpIsrael,” is said to have commenced on June 28, 2022, citing “steady attacks from Israel toward Palestinians.”
In the intervening period, GhostSec has carried out a range of attacks, together with individuals aimed at internet-exposed interfaces belonging to Bezeq International and an ELNet electricity meter positioned at the Scientific Industries Heart (Matam).

The breach of Berghof PLCs, considered in that mild, is component of the actor’s broader shift to strike the SCADA/ICS area, while it appears to be a scenario whereby the group took benefit of “quickly overlooked misconfigurations of industrial units” to have out the attacks.
“Inspite of the minimal effects of this incident, this is a great instance wherever a cyber attack could have easily been averted by easy, good configuration,” the researchers explained.
“Disabling the general public publicity of belongings to the Internet, and maintaining a excellent password plan, primarily switching the default login qualifications, would cause the hacktivists’ breach endeavor to fail.”
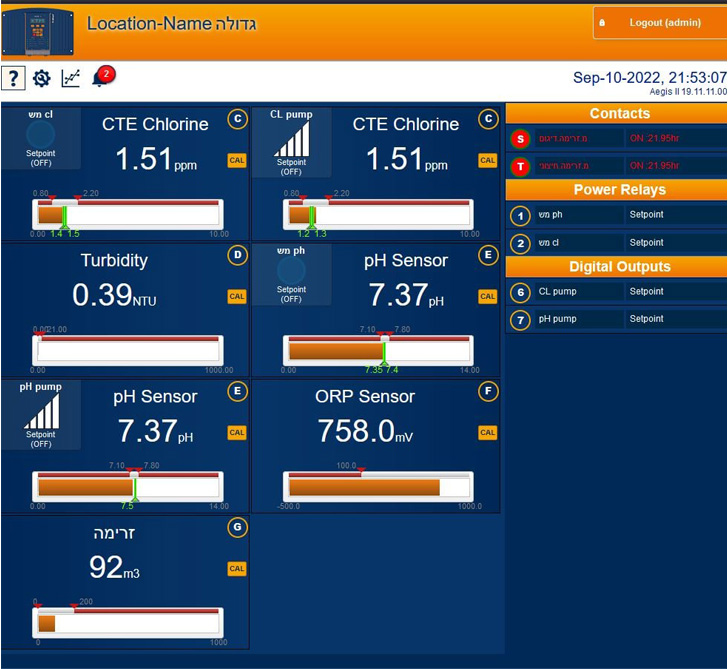
GhostSec, in the meanwhile, has continued to post a lot more screenshots, declaring to have received obtain to a different manage panel that can be utilised to alter chlorine and pH levels in the water.
“Hope you all can understand our final decision on not attacking their pH concentrations and risking a prospect to hurt the innocents of #Israel,” the group explained in a tweet posted more than the weekend. “Our’ war’ has often been FOR the people not versus them. #FreePalestine”
Found this posting fascinating? Abide by THN on Facebook, Twitter and LinkedIn to study more special material we post.
Some areas of this short article are sourced from:
thehackernews.com

 Why Vulnerability Scanning is Critical for SOC 2
Why Vulnerability Scanning is Critical for SOC 2