A new Golang-based peer-to-peer (P2P) botnet has been spotted actively concentrating on Linux servers in the education sector given that its emergence in March 2022.
Dubbed Panchan by Akamai Security Analysis, the malware “makes use of its crafted-in concurrency features to optimize spreadability and execute malware modules” and “harvests SSH keys to complete lateral movement.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The function-packed botnet, which depends on a essential listing of default SSH passwords to carry out a dictionary attack and expand its achieve, primarily functions as a cryptojacker created to hijack a computer’s methods to mine cryptocurrencies.
The cybersecurity and cloud services company observed it initially noticed Panchan’s action on March 19, 2022, and attributed the malware to a probably Japanese danger actor centered on the language employed in the administrative panel baked into the binary to edit the mining configuration.
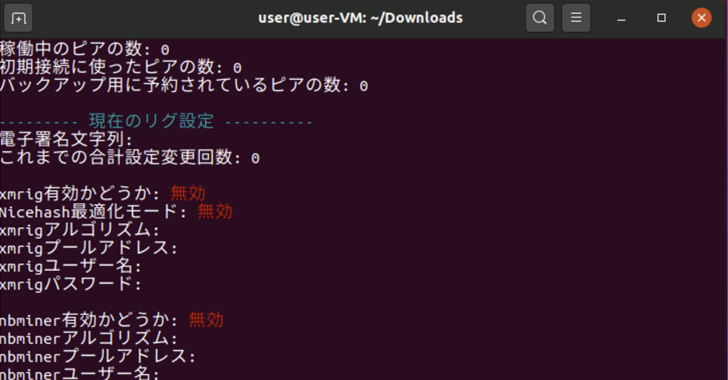
Panchan is acknowledged to deploy and execute two miners, XMRig and nbhash, on the host through runtime, the novelty remaining that the miners aren’t extracted to the disk to avoid leaving a forensic trail.
“To stay away from detection and cut down traceability, the malware drops its cryptominers as memory-mapped data files, devoid of any disk presence,” the scientists mentioned. “It also kills the cryptominer processes if it detects any procedure checking.”
Of the 209 contaminated friends detected so far, 40 are claimed to be at the moment active. Most of the compromised devices are situated in Asia (64), adopted by Europe (52), North America (45), South The us (11), Africa (1), and Oceania (1).

An fascinating clue as to the malware’s origins is the result of an OPSEC failure on the element of the risk actor, revealing the hyperlink to a Discord server that’s exhibited in the “godmode” admin panel.
“The primary chat was empty apart from a greeting of a further member that transpired in March,” the researchers said. “It could be that other chats are only accessible to increased privileged associates of the server.”
Uncovered this report interesting? Follow THN on Facebook, Twitter and LinkedIn to read extra exclusive articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Cloudflare mitigates biggest ever HTTPS DDos attack
Cloudflare mitigates biggest ever HTTPS DDos attack