A very little-acknowledged Russian-speaking cyber-espionage group has been joined to a new politically-inspired surveillance campaign concentrating on superior-position authorities officials, telecom products and services, and general public service infrastructures in Tajikistan.
The intrusion established, dubbed Paperbug by Swiss cybersecurity organization PRODAFT, has been attributed to a danger actor regarded as Nomadic Octopus (aka DustSquad).
“The sorts of compromised equipment range from individuals’ computers to [operational technology] units,” PRODAFT explained in a deep dive complex report shared with The Hacker News. “These targets make operation ‘Paperbug’ intelligence-driven.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The greatest motive behind the attacks is unclear at this stage, but the cybersecurity organization has elevated the chance that it could be the get the job done of opposition forces in the region or, alternatively, an intelligence-accumulating mission carried out by Russia or China.
Nomadic Octopus 1st came to mild in October 2018 when ESET and Kaspersky thorough a collection of phishing attacks mounted by the actor from several nations in Central Asia. The team is approximated to have been lively since at the very least 2014.
The cyber offensives have concerned the use of custom Android and Windows malware to strike a mix of higher-worth entities like community governments, diplomatic missions, and political bloggers, boosting the risk that the danger actor is possible involved in cyber surveillance operations.
The Windows malware, dubbed Octopus and which masqueraded as an choice edition of the Telegram messaging application, is a Delphi-centered instrument that enables the adversary to surveil victims, siphon sensitive information, and achieve backdoor obtain to their units by using a command-and-regulate (C2) panel.
A subsequent assessment by Gcow Security in December 2019 highlighted the innovative persistent danger (APT) group’s attacks versus the Ministry of International Affairs of Uzbekistan to deploy Octopus.
PRODAFT’s findings are the result of the discovery of an operational setting managed by Nomadic Octopus considering that 2020, making Paperbug the very first campaign orchestrated by the group since Octopus.
In accordance to details gathered by the corporation, the risk actor managed to obtain accessibility to a telecommunication business network, prior to shifting laterally to around a dozen targets focusing on govt networks, executives, and OT units with publicly acknowledged vulnerabilities. Precisely how and when the telecommunication network was infiltrated is unfamiliar.
“Procedure PaperBug aligns with the typical pattern of attacking into Central Asia federal government infrastructure that not long ago turned extra popular,” PRODAFT observed.
Nomadic Octopus is considered to exhibit some degree of cooperation with another Russian country-state actor regarded as Sofacy (aka APT28, Fancy Bear, Forest Blizzard, or FROZENLAKE), primarily based on victimology overlaps.
The most recent attacks further more entailed the use of an Octopus variant that comes with options to take screenshots, operate commands remotely, and down load and add data files to and from the infected host to a distant server. One such artifact was uploaded to VirusTotal on April 1, 2021.
Forthcoming WEBINARZero Belief + Deception: Study How to Outsmart Attackers!
Find out how Deception can detect state-of-the-art threats, stop lateral movement, and increase your Zero Have confidence in technique. Join our insightful webinar!
Help you save My Seat!
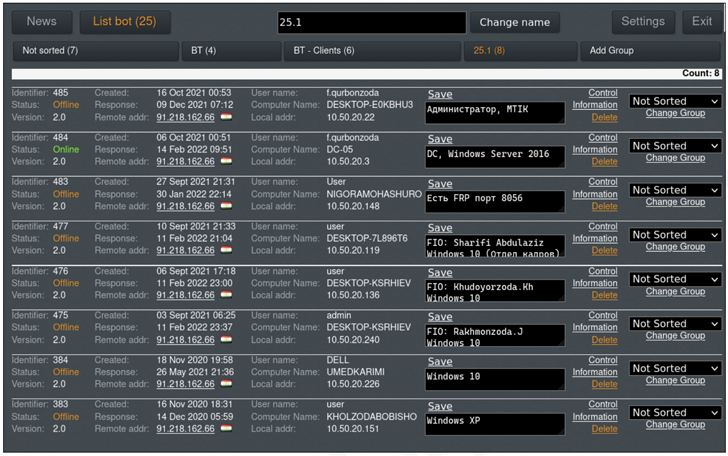
A nearer seem at the command-and-management (C2) server reveals that the group managed to effectively backdoor a complete of 499 programs as of January 27, 2022, some of which contain authorities network devices, fuel stations, and a cash register.
The group, nevertheless, won’t appear to possess advanced toolsets or be also involved about covering their tracks on sufferer devices inspite of the substantial-stakes mother nature of the attacks.
“As they operate on the compromised equipment to steal information, they occasionally inadvertently caused permission pop-ups on target computers, which resulted in suspicion from the sufferer,” the organization pointed out. “Even so, this was solved thanks to the team diligently naming the information they transfer as benign and inconspicuous programs.”
The similar tactic extends to naming their malicious equipment as properly, what with the group camouflaging them as preferred web browsers such as Google Chrome, Mozilla Firefox, and Yandex to fly under the radar.
That having stated, Paperbug attack chains are mainly characterised by the use of general public offensive instruments and generic techniques, correctly performing as a “cloak” for the group and making attribution a lot more challenging.
“This imbalance among the operator abilities and importance of the mission could possibly suggest that the operators have been recruited by some entity which furnished them a listing of commands that need to have to be executed on just about every device exactly,” PRODAFT mentioned, including “the operator follows a checklist and is forced to stick to it.”
Observed this short article appealing? Adhere to us on Twitter and LinkedIn to go through extra exceptional content we put up.
Some areas of this report are sourced from:
thehackernews.com


 LimeRAT Malware Analysis: Extracting the Config
LimeRAT Malware Analysis: Extracting the Config