A cybercrime group acknowledged for targeting e-commerce websites unleashed a “multi-phase destructive marketing campaign” previously this calendar year developed with an intent to distribute info stealers and JavaScript-centered payment skimmers.
In a new report revealed today and shared with The Hacker News, Singapore-centered cybersecurity company Group-IB attributed the procedure to the exact team that’s been linked to a separate attack aimed at on the net merchants making use of password-thieving malware to infect their websites with FakeSecurity JavaScript-sniffers (JS-sniffers).
The marketing campaign progressed in 4 waves, starting in February and ending in September, with the operators relying on specifically-crafted phishing internet pages and lure documents laced with malicious macros to obtain Vidar and Raccoon information stealers on to victim units.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The supreme purpose of the attack, the scientists observed, was to steal payment and person info by way of a number of attack vectors and resources to deliver the malware.
The fake web pages had been developed using the Mephistophilus phishing kit, which makes it possible for attackers to produce and deploy phishing landing pages engineered for distributing malware.
“Attackers despatched backlinks to phony internet pages that educated victims about a missing plugin expected to exhibit the document correctly,” Group-IB researchers stated in an assessment of the cybercrime group’s tactics final November. “If a consumer downloaded the plugin, their computer system was contaminated with the password-stealing malware.”
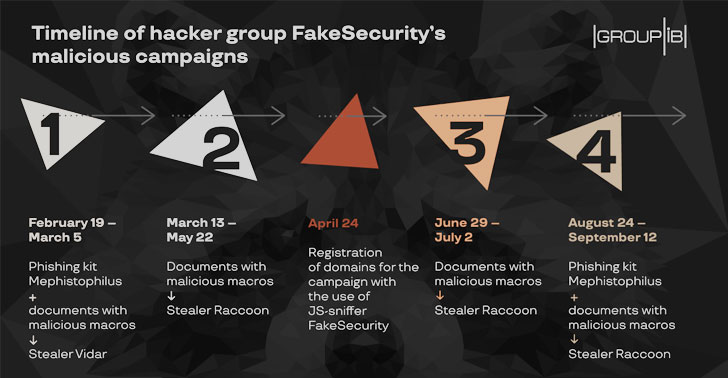
Even though the very first wave of the marketing campaign in February and March sent the Vidar password stealer to intercept passwords from person browsers and a variety of applications, subsequent iterations switched to the Raccoon stealer and AveMaria RAT to meet its objectives.
Raccoon, initially documented by Cybereason final yr, will come with a extensive array of abilities and communicates with a command-and-regulate (C2) server to siphon knowledge — including screenshots, credit card details, cryptocurrency wallets, saved browser passwords, e-mails, and program details.
Raccoon is also one of a kind in that it bypasses the blocking of lively C2 servers by producing a request to a Telegram channel (“blintick”) in order to get the encrypted tackle of the C2 server, aside from giving 24×7 consumer aid to local community issues and reviews by means of the chat assistance.
AveMaria RAT, likewise, is able of ensuring persistence, recording keystrokes, injecting malicious code, and exfiltrating sensitive information, among other folks.
Both of those Vidar and Raccoon are offered as malware-as-a-service (MaaS) on underground discussion boards. The rental price tag for Vidar stealer ranges from $250 to $300 per thirty day period, while the latter fees $200 a thirty day period to use.
Together with the 4 levels described over, Group-IB also noticed an interim stage amongst Might to September 2020, during when as quite a few as 20 on the internet suppliers have been infected with a modified JS-sniffer of the FakeSecurity spouse and children.
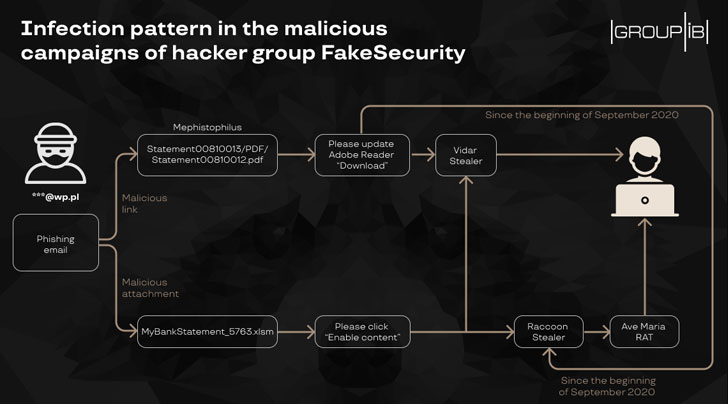
Apparently, the infrastructure utilised to distribute the Vidar and Raccoon stealers had been reused to store the sniffer code and obtain stolen lender card data, top the scientists to url the two campaigns.
The advancement is yet an additional indicator that adversaries are stepping up their efforts to compromise on the net marketplaces to pilfer shopper payment data, even as regulation enforcement businesses are doing the job to tackle cybercrime.
Previously this January, the Interpol, performing on electronic forensic evidence from Group-IB, nabbed a few persons associated with a group referred to as “GetBilling” as component of an procedure codenamed Night time Fury for running a JS-sniffer campaign in Indonesia.
Observed this write-up intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to go through much more special information we put up.
Some components of this post are sourced from:
thehackernews.com

 Kmart, a vulnerable target, among those hit in Egregor ransomware attack spree
Kmart, a vulnerable target, among those hit in Egregor ransomware attack spree