Nicknamed ProxyNotShell, a new exploit applied in the wild requires gain of the a short while ago posted Microsoft Server-Aspect Ask for Forgery (SSRF) vulnerability CVE-2022-41040 and a 2nd vulnerability, CVE-2022-41082 that will allow Remote Code Execution (RCE) when PowerShell is obtainable to unknown attackers.
Dependent on ProxyShell, this new zero-day abuse risk leverage a chained attack very similar to the a single applied in the 2021 ProxyShell attack that exploited the combination of a number of vulnerabilities – CVE-2021-34523, CVE-2021-34473, and CVE-2021-31207 – to permit a distant actor to execute arbitrary code.
Regardless of the probable severity of attacks employing them, ProxyShell vulnerabilities are still on CISA’s checklist of major 2021 routinely exploited vulnerabilities.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Meet ProxyNotShell
Recorded on September 19, 2022, CVE-2022-41082 is an attack vector targeting Microsoft’s Exchange Servers, enabling attacks of small complexity with small privileges needed. Impacted expert services, if susceptible, allow an authenticated attacker to compromise the fundamental exchange server by leveraging existing exchange PowerShell, which could consequence in a full compromise.
With the aid of CVE-2022-41040, an additional Microsoft vulnerability also recorded on September 19, 2022, an attacker can remotely set off CVE-2022-41082 to remotely execute instructions.
Nevertheless a user requires to have the privilege to accessibility CVE-2022-41040, which must curtail the vulnerability accessibility to attackers, the essential amount of privilege is small.
At the time of crafting, Microsoft has not nonetheless issued a patch but recommends that users include a blocking rule as a mitigation evaluate.
Equally vulnerabilities were uncovered for the duration of an lively attack from GTSC, a Vietnamese group termed GTSC, granting attackers obtain to some of their clients. Though neither vulnerability on its personal is especially unsafe, exploits chaining them jointly could perhaps lead to catastrophic breaches.
The chained vulnerabilities could grant an outsider attacker the capacity to browse e-mails instantly off an organization’s server the means to breach the group with CVE-2022-41040 Distant Code Execution and implant malware on the organization’s Exchange Server with CVE-2022-41082.
Even though it appears that attackers would require some stage of authentication to activate the chained vulnerabilities exploit, the correct stage of authentication needed – rated “Low” by Microsoft – is not yet clarified. Nonetheless, this required low authentication degree need to effectively protect against a huge, automatic attack focusing on every Trade server all around the world. This hopefully will reduce a replay of the 2021 ProxyShell debacle.
However, acquiring a single legitimate email address/password mix on a supplied Exchange server really should not be overly challenging, and, as this attack bypasses MFA or FIDO token validation to log into Outlook Web Accessibility, a one compromised email handle/password mixture is all that is needed.
Mitigating ProxyNotShell Exposure
At the time of crafting, Microsoft has not however issued a patch but suggests that buyers incorporate a blocking rule as a mitigation measure of mysterious efficacy.
Blocking incoming site visitors to Exchange Servers holding critical asserts is also an possibility, however only practicable if such a measure does not influence crucial functions and should really preferably be perceived as a temporary measure pending Microsoft’s issuance of a confirmed patch.
Assessing ProxyNotShell Exposure
As the present-day mitigation possibilities are possibly of unverified efficacy or possibly detrimental to the clean functioning of operations, analyzing the diploma of exposure to ProxyNotShell may possibly stop getting likely disruptive needless preventative actions, or show which property to preemptively migrate to unexposed servers.
Cymulate Research Lab has made a custom made-designed evaluation for ProxyNotShell that enable companies to estimate accurately their diploma of publicity to ProxyNotShell.
A ProxyNotShell attack vector has been included to the sophisticated scenarios templates, and operating it on your natural environment yields the needed info to validate exposure – or absence thereof – to ProxyNotShell.
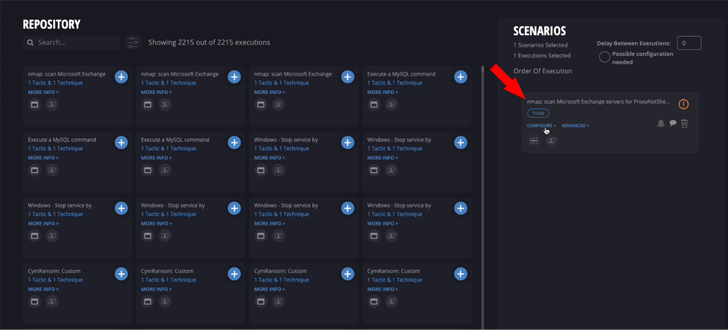
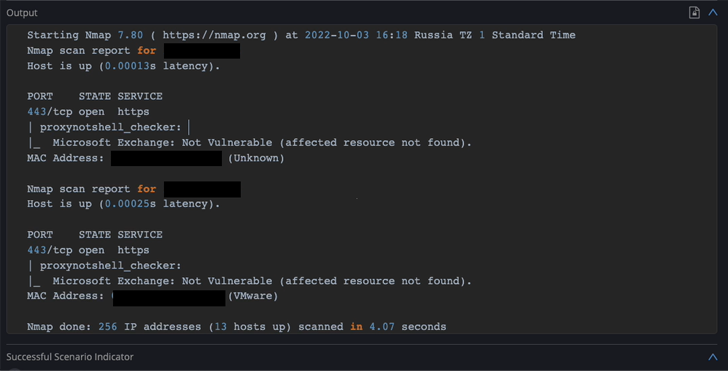
Until verified patches are offered from Microsoft, evaluating exposure to ProxyNotShell to consider particularly which servers are likely targets is the most price tag-economical way to consider exactly which property are uncovered and devise focused preemptive steps with utmost impact.
By Cymulate Investigation Labs
Located this short article appealing? Observe THN on Facebook, Twitter and LinkedIn to examine much more exclusive content we submit.
Some sections of this article are sourced from:
thehackernews.com


 Optus Hack Exposes Data of Nearly 2.1 Million Australian Telecom Customers
Optus Hack Exposes Data of Nearly 2.1 Million Australian Telecom Customers