Authorities entities in Asia-Pacific and North The us are getting targeted by an not known risk actor with an off-the-shelf malware downloader recognised as PureCrypter to produce an array of data stealers and ransomware.
“The PureCrypter campaign takes advantage of the domain of a compromised non-earnings business as a command-and-control (C2) to supply a secondary payload,” Menlo Security researcher Abhay Yadav reported.
The distinctive types of malware propagated applying PureCrypter contain RedLine Stealer, Agent Tesla, Eternity, Blackmoon (aka KRBanker), and Philadelphia ransomware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Initial documented in June 2022, PureCrypter is marketed for sale by its writer for $59 for one-month accessibility (or $245 for a just one-off life span obtain) and is capable of distributing a multitude of malware.
In December 2022, PureCoder – the developer guiding the application – expanded the slate of choices to contain a logger and data stealer regarded as PureLogs, which is built to siphon info from web browsers, crypto wallets, and email shoppers. It fees $99 a yr (or $199 for life span entry).
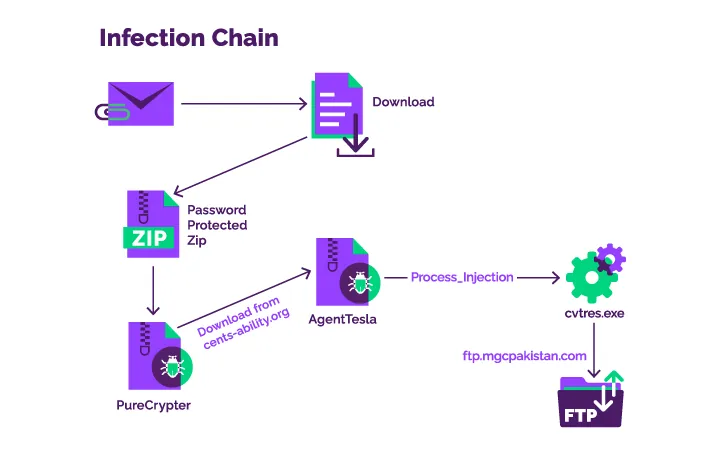
The infection sequence in-depth by Menlo Security commences with a phishing email that contains a Discord URL that points to the very first-phase ingredient, a password-safeguarded ZIP archive that, in change, hundreds the PureCrypter malware.
The loader, for its section, reaches out to the web site of the breached non-profit entity to fetch the secondary payload, which is a .NET-based keylogger named Agent Tesla.
The backdoor then establishes a relationship to an FTP server located in Pakistan to exfiltrate the harvested facts, indicating that compromised credentials might have been utilised to complete the exercise.
Uncovered this write-up attention-grabbing? Observe us on Twitter and LinkedIn to examine more distinctive articles we submit.
Some parts of this report are sourced from:
thehackernews.com


 Governments Targeted by Discord-Based Threat Campaign
Governments Targeted by Discord-Based Threat Campaign