A “substantial and resilient infrastructure” comprising above 250 domains is staying used to distribute details-stealing malware these kinds of as Raccoon and Vidar considering that early 2020.
The an infection chain “takes advantage of about a hundred of phony cracked application catalogue websites that redirect to numerous one-way links in advance of downloading the payload hosted on file share platforms, these kinds of as GitHub,” cybersecurity firm SEKOIA said in an examination posted before this month.
The French cybersecurity organization assessed the domains to be operated by a danger actor jogging a targeted traffic path system (TDS), which permits other cybercriminals to hire the provider to distribute their malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attacks concentrate on people hunting for cracked versions of program and game titles on search engines like Google, surfacing fraudulent sites on top by leveraging a approach termed search motor optimization (Website positioning) poisoning to lure victims into downloading and executing the destructive payloads.
The poisoned final result comes with a obtain url to the promised software program that, upon clicking, triggers a five-stage URL redirection sequence to acquire the consumer to a web site exhibiting a shortened hyperlink, which points to a password-protected RAR archive file hosted on GitHub, together with its password.
“Applying various redirections complicates automated evaluation by security options,” the scientists stated. “Carving the infrastructure as these is just about absolutely built to make certain resilience, building it simpler and faster to update or transform a move.”
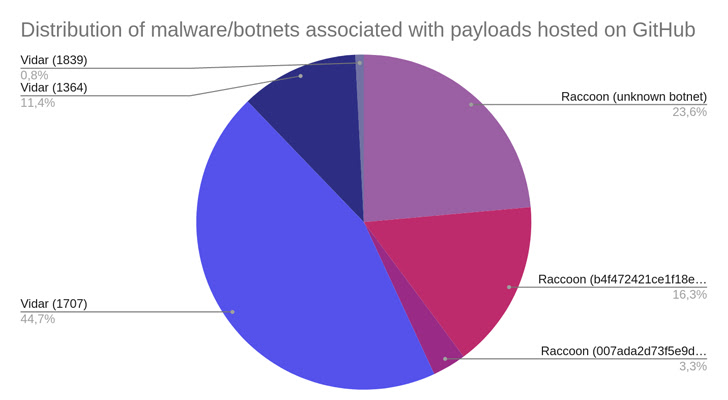
Ought to the victim uncompress the RAR archive and operate the purported set up executable contained within just it, possibly of the two malware people, Raccoon or Vidar, are set up on the method.
The enhancement comes as Cyble comprehensive a rogue Google Advertisements marketing campaign that employs commonly-made use of software program these types of as AnyDesk, Bluestacks, Notepad++, and Zoom as lures to provide a characteristic-rich stealer known as Rhadamanthys Stealer.
An alternate variant of the attack chain has been noticed having gain of phishing e-mails masquerading as lender statements to dupe unwitting consumers into clicking on fraudulent one-way links.
Fabricated web-sites impersonating the common remote desktop option have also been place to use in the previous to propagate a Python-based mostly details stealer dubbed Mitsu Stealer.
Both pieces of malware are outfitted to siphon a extensive range of particular info from compromised machines, harvest credentials from web browsers, and steal information from different cryptocurrency wallets.
Customers are suggested to refrain from downloading pirated software and implement multi-factor authentication anywhere probable to harden accounts.
“It is essential for customers to training warning when receiving spam e-mails or to check out phishing sites and to validate the source right before downloading any purposes,” the researchers claimed.
Uncovered this article intriguing? Abide by us on Twitter and LinkedIn to read through additional special written content we submit.
Some pieces of this article are sourced from:
thehackernews.com

 A Secure User Authentication Method – Planning is More Important than Ever
A Secure User Authentication Method – Planning is More Important than Ever