A new report has identified that international ransomware exercise dropped throughout the third quarter as the get of dominant teams in the landscape shifted, but that organizations must anticipate a surge by danger actors in Q4 to exploit consumer trends.
The number of ransomware attacks in Q3 2022 was down 10.5% on Q2, in accordance to the most recent report by cyber security firm Digital Shadows. This was pushed in portion by the unexpected cessation of action by the Conti group, as effectively as a reorganisation of major groups above July and August.
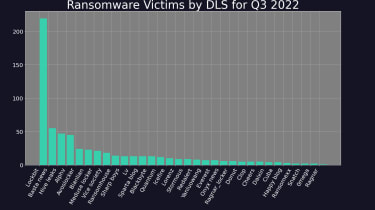
LockBit 3., the most up-to-date pressure by the LockBit group of threat actors, consolidated its guide across the landscape in Q3, accounting for 35.1% of all exercise throughout the period of time, compared to 32.8% in Q2. The group’s rise, even as its all round action declined, has been matched by the expansion of a quantity of new teams, together with Black Basta, Hive Leaks, and Alphv, which account for 9%, 8%, and 7% of activity respectively.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Digital Shadows implies that these teams have straight taken gain of the gap in the market remaining by Conti, which immediately after threatening to overthrow the Costa Rican governing administration in May, seemingly shut down in June. The group’s website has disappeared, and a drop off in action correct at the conclude of Q2 has been joined specifically to the group’s clear cessation of attacks.
Groups that bucked the craze with amplified activity across the period consist of ‘AvosLocker’ (up 50%) and Hive Leaks (up 80.8%). The latter operates the Hive payload, which was singled out by Microsoft in Q3 for its subtle features, and for being penned in the programming language Rust, which is getting to be a common programming language for hacker groups.
Some in the cyber security community have recommended that Hive is composed of former Conti actors, or is even a continuation of the same group. Investigative journalist and cyber crime pro Brian Krebs tweeted that attacks on Costa Rica appeared to have been committed by Hive, but that “with Conti seemingly in the method of rebranding, it could just as effectively be the similar criminals included.”
Nevertheless, Emisoft risk analyst Brett Callow subsequently tweeted a screenshot from Hive’s site that states “we are not linked with Conti”. No evidence yet hyperlinks any rising team with Conti.
Around 39% of all attacks throughout Q3 ended up produced against victims within the United States, reflective of the consolidation of rich providers in the place. France and Spain adopted, with the UK the fourth most qualified in the exact same period, accounting for 4.8% of victims. This marks a fall from the UK’s third location in Q2, and seems to have been pushed by a surge in attacks in France and Spain, which include Hive’s attack on French telco giant Altice in August.
In fact, while nearly all nations around the world noticed lessened ransomware attacks in Q3, France, Spain and Israel noticed rises. Spain was an outlier, with a 66% rise in ransomware action throughout the quarter tied to a surge by the group ‘Sparta Website.’
The industrial items and services sector remained the most focused sector through the interval, recording virtually double the attacks of the technology sector, the next most qualified. As the war in Ukraine drags on, attacks on provide chains and critical nationwide infrastructure (CNI) carry on to increase, and state-backing of ransomware attacks will continue to enhance these action.
Bracing for a rise in Q4
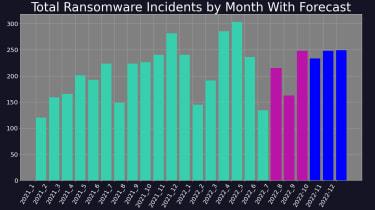
Electronic Shadows forecasts a increase in action in Q4 2022. This is not unusual, as professional situations this sort of as Black Friday and Cyber Monday usually coincide with an boost in destructive exercise on-line, although on-line buying all around Xmas is exploited by menace actors with phishing campaigns.
Right after falling prey to a dispersed denial of support (DDoS) attack in August, which took down its internet site for many times, the LockBit team vowed to be ‘more aggressive’ and stated that it was recruiting new customers. This could be connected to the raise of attacks at the close of Q3, and indeed the LockBit group observed its highest ever share of worldwide ransomware activity at 40%.
Issues have also been lifted because of to the alleged leak of a LockBit 3. ‘builder’ in September. If reputable, this would enable rival threat actors to build their very own variation of LockBit ransomware, and as these types of the leak could precede a spike in use of the highly-effective malware throughout Q4 and outside of.
Some sections of this posting are sourced from:
www.itpro.co.uk


 Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox
Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox