Cybercriminals are increasingly outsourcing the endeavor of deploying ransomware to affiliates applying commodity malware and attack instruments, according to new investigate.
In a new investigation printed by Sophos currently and shared with The Hacker News, new deployments of Ryuk and Egregor ransomware have included the use of SystemBC backdoor to laterally go throughout the network and fetch extra payloads for even more exploitation.
Affiliates are usually risk actors dependable for getting an initial foothold in a focus on network.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“SystemBC is a frequent aspect of the latest ransomware attackers’ toolkits,” said Sophos senior risk researcher and previous Ars Technica national security editor Sean Gallagher.
“The backdoor can be utilized in mix with other scripts and malware to execute discovery, exfiltration and lateral movement in an automatic way throughout numerous targets. These SystemBC capabilities have been initially supposed for mass exploitation, but they have now been folded into the toolkit for specific attacks — such as ransomware.”
Initially documented by Proofpoint in August 2019, SystemBC is a proxy malware that leverages SOCKS5 internet protocol to mask traffic to command-and-control (C2) servers and download the DanaBot banking Trojan.
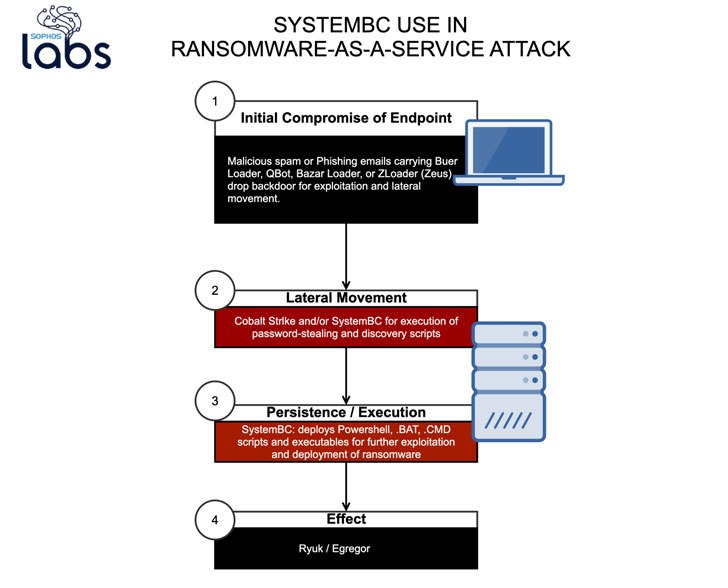
The SystemBC RAT has due to the fact expanded the breadth of its toolset with new traits that let it to use a Tor relationship to encrypt and conceal the destination of C2 communications, therefore offering attackers with a persistent backdoor to start other attacks.
Scientists notice that SystemBC has been utilized in a quantity of ransomware attacks — typically in conjunction with other write-up-exploitation applications like CobaltStrike — to take benefit of its Tor proxy and distant entry options to parse and execute destructive shell instructions, VBS scripts, and other DLL blobs sent by the server about the anonymous link.
It also appears that SystemBC is just a single of the quite a few commodity tools that are deployed as a consequence of original compromise stemming from phishing email messages that produce malware loaders like Buer Loader, Zloader, and Qbot — foremost the scientists to suspect that the attacks may well have been released by affiliates of the ransomware operators, or by the ransomware gangs by themselves by means of many malware-as-a-provider companies.
“These abilities give attackers a place-and-shoot capability to complete discovery, exfiltration and lateral movement with packaged scripts and executables — devoid of getting to have fingers on a keyboard,” the researchers mentioned.
The rise of commodity malware also points to a new pattern the place ransomware is provided as a provider to affiliates, like it can be in the scenario of MountLocker, wherever the operators supply double extortion abilities to affiliates so as to distribute the ransomware with nominal hard work.
“The use of multiple equipment in ransomware-as-a-support attacks makes an ever additional varied attack profile that is more difficult for IT security groups to forecast and offer with,” Gallagher reported. “Protection-in-depth, employee instruction and human-based mostly risk looking are vital to detecting and blocking these attacks.”
Located this article exciting? Adhere to THN on Fb, Twitter and LinkedIn to read far more distinctive written content we put up.
Some pieces of this report are sourced from:
thehackernews.com

 Most retailers stepped up IT security for the holiday season
Most retailers stepped up IT security for the holiday season