As ransomware bacterial infections have developed from purely encrypting details to techniques this kind of as double and triple extortion, a new attack vector is very likely to set the stage for upcoming strategies.
Named Ransomware for IoT or R4IoT by Forescout, it truly is a “novel, proof-of-concept ransomware that exploits an IoT system to acquire access and transfer laterally in an IT [information technology] network and effects the OT [operational technology] network.”
This potential pivot is primarily based on the quick advancement in the variety of IoT units as well as the convergence of IT and OT networks in organizations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

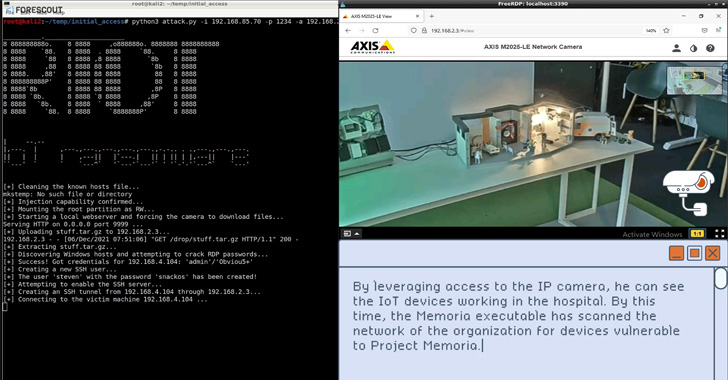
The final target of R4IoT is to leverage exposed and susceptible IoT equipment these types of as IP cameras to acquire an preliminary foothold, adopted by deploying ransomware in the IT network and taking edge of bad operational security tactics to hold mission-critical procedures hostage.
“By compromising IoT, IT, and OT assets, R4IoT goes past the standard encryption and details exfiltration to result in physical disruption of business functions,” the researchers claimed, thus introducing an further layer of extortion to a standard ransomware attack.
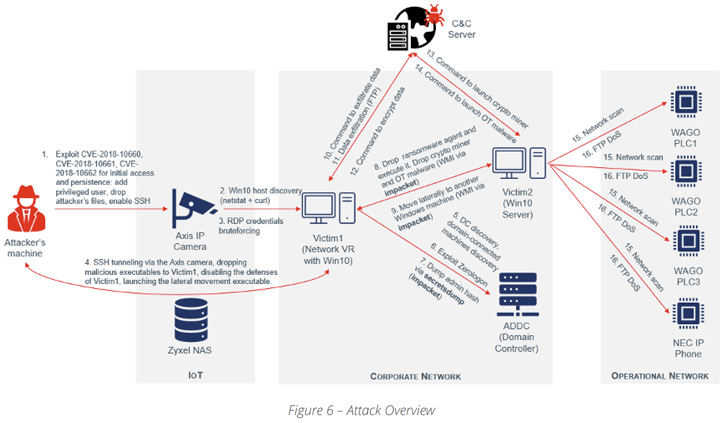
Put in a different way, R4IoT is a new kind of malware that brings with each other an IoT entry point and ransomware-related lateral motion and encryption on an IT network, causing an prolonged influence on both equally IT and OT networks.
In a hypothetical scenario, this could entail compromising a device in the corporate network to not only drop ransomware but also retrieve added payloads from a distant server to deploy cryptocurrency miners and start denial-of-support (DoS) attacks towards OT assets.

To mitigate each the probability and the influence of opportunity R4IoT incidents, companies are advisable to identify and patch susceptible devices, enforce network segmentation, put into action robust password procedures, and check HTTPS connections, FTP periods, and network site visitors.
“Ransomware has been the most widespread menace of the previous couple of several years, and so far, it has mostly leveraged vulnerabilities in regular IT tools to cripple companies,” the scientists concluded.
“But new connectivity developments have extra a number and a diversity of OT and IoT equipment that have greater risk in nearly every single small business.”
Uncovered this post fascinating? Comply with THN on Facebook, Twitter and LinkedIn to read through additional unique written content we write-up.
Some elements of this posting are sourced from:
thehackernews.com

 Scammers Target NFT Discord Channel
Scammers Target NFT Discord Channel