Amazon Web Expert services (AWS) has settled a cross-tenant vulnerability in its system that could be weaponized by an attacker to gain unauthorized entry to sources.
The issue relates to a confused deputy dilemma, a variety of privilege escalation wherever a software that will not have permission to carry out an action can coerce a extra-privileged entity to accomplish the motion.
The shortcoming was described by Datadog to AWS on September 1, 2022, pursuing which a patch was shipped on September 6.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“This attack abuses the AppSync services to believe [identity and access management] roles in other AWS accounts, which enables an attacker to pivot into a target organization and accessibility resources in people accounts,” Datadog researcher Nick Frichette reported in a report released past week.

In a coordinated disclosure, Amazon said that no buyers have been impacted by the vulnerability and that no consumer motion is necessary.
It explained it as a “case-sensitivity parsing issue in just AWS AppSync, which could possibly be made use of to bypass the service’s cross-account job usage validations and acquire motion as the assistance across buyer accounts.”
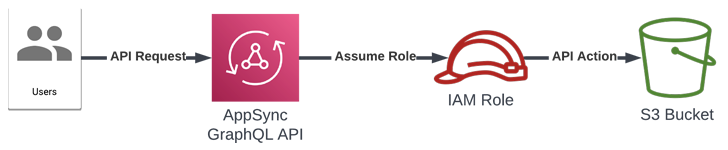
AWS AppSync gives developers GraphQL APIs to retrieve or modify info from various facts resources as very well as routinely sync details involving cell and web programs and the cloud.
The support can also be used to combine with other AWS solutions through unique roles intended to conduct the essential API phone calls with the essential IAM permissions.
Whilst AWS does have safeguards in put to prevent AppSync from assuming arbitrary roles by validating the role’s Amazon Resource Title (ARN), the trouble stems from the simple fact that the verify could be trivially bypassed by passing the “serviceRoleArn” parameter in a decrease scenario.
This actions could then be exploited to offer the identifier of a function in a unique AWS account.
“This vulnerability in AWS AppSync allowed attackers to cross account boundaries and execute AWS API phone calls in victim accounts by means of IAM roles that reliable the AppSync support,” Frichette mentioned.
“By making use of this approach, attackers could breach organizations that utilised AppSync and acquire entry to sources linked with those roles.”
Identified this write-up fascinating? Comply with THN on Facebook, Twitter and LinkedIn to read a lot more exceptional content we post.
Some components of this posting are sourced from:
thehackernews.com


 The 5 Cornerstones for an Effective Cyber Security Awareness Training
The 5 Cornerstones for an Effective Cyber Security Awareness Training