Days after F5 launched patches for a critical distant code execution vulnerability affecting its Huge-IP household of products and solutions, security scientists are warning that they ended up capable to generate an exploit for the shortcoming.
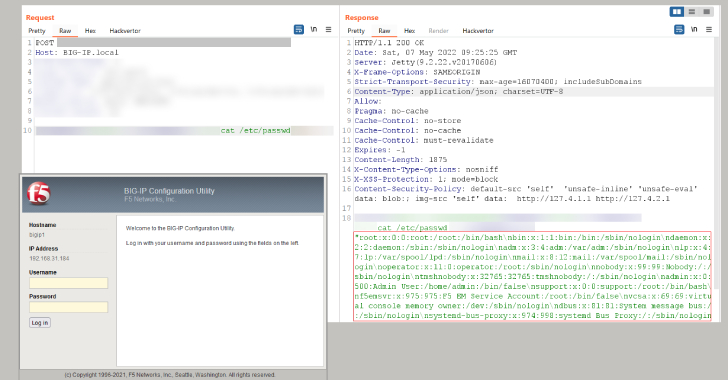
Tracked CVE-2022-1388 (CVSS rating: 9.8), the flaw relates to an iControl Relaxation authentication bypass that, if correctly exploited, could lead to distant code execution, making it possible for an attacker to achieve initial access and just take regulate of an influenced process.
This could variety anywhere from deploying cryptocurrency miners to deploying web shells for follow-on attacks, this kind of as facts theft and ransomware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“We have reproduced the refreshing CVE-2022-1388 in F5’s Large-IP,” cybersecurity enterprise Beneficial Technologies mentioned in a tweet on Friday. “Patch ASAP!”
The critical security vulnerability impacts the next versions of Massive-IP merchandise –
- 16.1. – 16.1.2
- 15.1. – 15.1.5
- 14.1. – 14.1.4
- 13.1. – 13.1.4
- 12.1. – 12.1.6
- 11.6.1 – 11.6.5
Fixes are offered in versions 17.., 16.1.2.2, 15.1.5.1, 14.1.4.6, and 13.1.5. Firmware versions 11.x and 12.x will not get security updates and end users relying on all those versions should look at upgrading to a newer variation or implement the workarounds –
- Block iControl Relaxation obtain by means of the self IP deal with
- Block iControl Rest accessibility by means of the administration interface, and
- Modify the Major-IP httpd configuration
Last month, cybersecurity authorities from Australia, Canada, New Zealand, the U.K., and the U.S. jointly warned that “risk actors aggressively specific recently disclosed critical software package vulnerabilities versus broad target sets, such as public and personal sector corporations all over the world.”
With the F5 Large-IP flaw located trivial to exploit, malicious hacking crews are expected to abide by fit, creating it very important that influenced companies implement the patches.
Uncovered this article exciting? Observe THN on Facebook, Twitter and LinkedIn to browse much more distinctive material we write-up.
Some sections of this report are sourced from:
thehackernews.com

 U.S. Sanctions Cryptocurrency Mixer Blender for Helping North Korea Launder Millions
U.S. Sanctions Cryptocurrency Mixer Blender for Helping North Korea Launder Millions