Microsoft on Tuesday reported it addressed an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB that enabled total examine and compose entry.
The tech large stated the problem was introduced on August 12, 2022, and rectified throughout the world on October 6, 2022, two times right after dependable disclosure from Orca Security, which dubbed the flaw CosMiss.
“In brief, if an attacker experienced understanding of a Notebook’s ‘forwardingId,’ which is the UUID of the Notebook Workspace, they would have experienced full permissions on the Notebook without acquiring to authenticate, together with read through and publish entry, and the ability to modify the file technique of the container operating the notebook,” researchers Lidor Ben Shitrit and Roee Sagi claimed.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
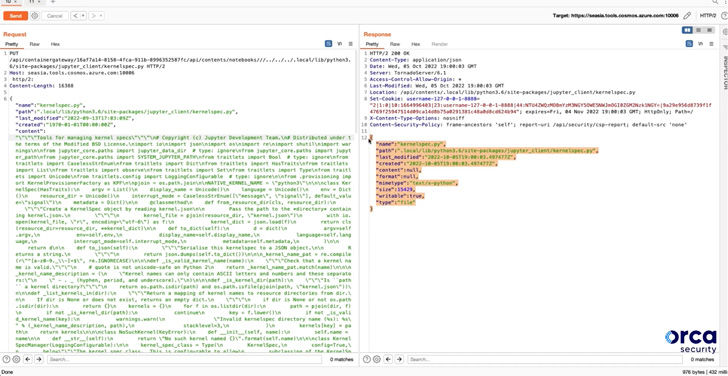
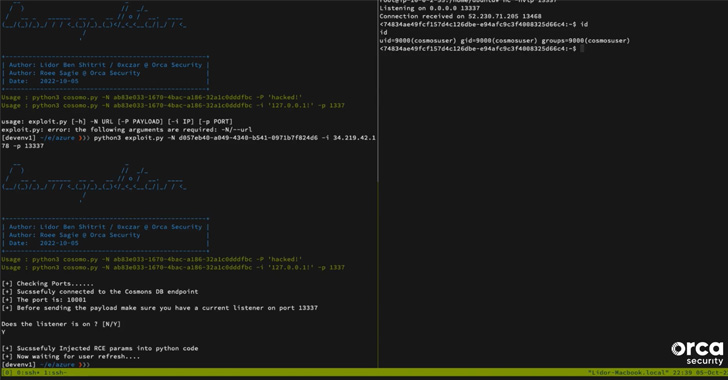
This container modification could in the end pave the way for getting remote code execution in the Notebook container by overwriting a Python file related with the Cosmos DB Explorer to spawn a reverse shell.

Effective exploitation of the flaw, on the other hand, necessitates that the adversary is in possession of the one of a kind 128-bit forwardingId and that it can be place to use inside a a person-hour window, just after which the short-term Notebook is routinely deleted.
“The vulnerability, even with know-how of the forwardingId, did not give the capability to execute notebooks, quickly preserve notebooks in the victim’s (optional) related GitHub repository, or obtain to data in the Azure Cosmos DB account,” Redmond claimed.
Microsoft pointed out in its own advisory that it recognized no proof of malicious action, including no motion is essential from consumers. It also explained the issue as “tough to exploit” owing to the randomness of the 128 bit forwadingID and its confined lifespan.
“Buyers not working with Jupyter Notebooks (99.8% of Azure Cosmos DB consumers do NOT use Jupyter notebooks) were not inclined to this vulnerability,” it even further said.
Located this report attention-grabbing? Stick to THN on Fb, Twitter and LinkedIn to read extra distinctive articles we put up.
Some parts of this report are sourced from:
thehackernews.com

 LockBit Dominates Ransomware Campaigns in 2022: Deep Instinct
LockBit Dominates Ransomware Campaigns in 2022: Deep Instinct