A new information stealer known as Stealc that’s currently being marketed on the dark web could arise as a worthy competitor to other malware of its ilk.
“The threat actor offers Stealc as a completely featured and ready-to-use stealer, whose growth relied on Vidar, Raccoon, Mars, and RedLine stealers,” SEKOIA reported in a Monday report.
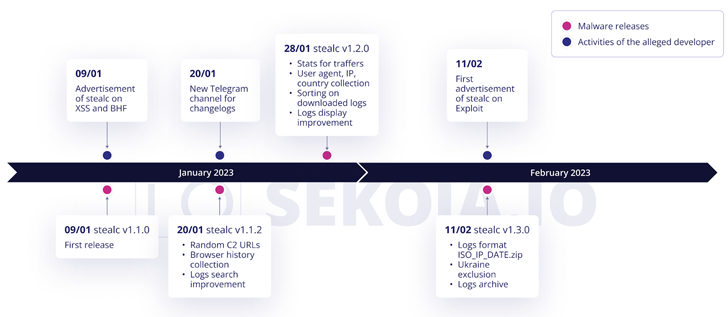
The French cybersecurity corporation explained it identified a lot more than 40 Stealc samples dispersed in the wild and 35 energetic command-and-manage (C2) servers, suggesting that the malware is now gaining traction among criminal teams.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Stealc, very first promoted by an actor named Plymouth on the XSS and BHF Russian-speaking underground community forums on January 9, 2023, is written in C and will come with capabilities to steal details from web browsers, crypto wallets, email clientele, and messaging applications.
The malware-as-a-assistance (MaaS) also features of a “customizable” file grabber that allows its buyers to tailor the module to siphon data files of interest. It further implements loader capabilities to deploy further payloads.
SEKOIA assessed with “substantial self esteem that its alleged developer rapidly proven itself as a reliable threat actor, and its malware gained the have confidence in of cybercriminals working with infostealers.”
Amongst the distribution vectors used to supply Stealc are YouTube movies posted from compromised accounts that connection to a website peddling cracked software package (“rcc-software[.]com”).
This also implies that consumers browsing for means to put in pirated application on YouTube are a goal, mirroring the exact same tactic adopted by an additional infostealer dubbed Aurora.
“Given that buyers of the Stealc MaaS own a make of its administration panel to host the stealer C2 server and produce stealer samples by themselves, it is most likely that the establish will leak into the underground communities in the medium term,” the organization included.
In accordance to antivirus vendor Avast, FormBook, Agent Tesla, RedLine, LokiBot, Raccoon, Snake Keylogger, and Arkei (along with its fork Vidar) accounted for the most common stealer malware strains through Q4 2022.
Identified this article fascinating? Adhere to us on Twitter and LinkedIn to study much more unique written content we post.
Some parts of this posting are sourced from:
thehackernews.com


 Fifth of Brits Have Fallen Victim to Online Scammers
Fifth of Brits Have Fallen Victim to Online Scammers