Cybersecurity scientists have unearthed a fourth new malware strain—designed to unfold the malware on to other computer systems in victims’ networks—which was deployed as part of the SolarWinds supply chain attack disclosed late past 12 months.
Dubbed “Raindrop” by Broadcom-owned Symantec, the malware joins the likes of other destructive implants these kinds of as Sunspot, Sunburst (or Solorigate), and Teardrop that ended up stealthily shipped to business networks.
The latest finding will come amid a ongoing probe into the breach, suspected to be of Russian origin, that has claimed a range of U.S. govt agencies and non-public sector organizations.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The discovery of Raindrop is a substantial phase in our investigation of the SolarWinds attacks as it gives further insights into article-compromise exercise at corporations of interest to the attackers,” Symantec researchers said.
The cybersecurity organization mentioned it uncovered only 4 samples of Raindrop to date that ended up utilized to supply the Cobalt Strike Beacon — an in-memory backdoor capable of command execution, keylogging, file transfer, privilege escalation, port scanning, and lateral motion.
Symantec, previous month, experienced uncovered more than 2,000 programs belonging to 100 prospects that acquired the trojanized SolarWinds Orion updates, with find targets contaminated with a 2nd-stage payload called Teardrop which is also utilised to set up the Cobalt Strike Beacon.
“The way Teardrop is developed, it could have dropped something in this scenario, it dropped Beacon, a payload integrated with Cobalt Strike,” Check Stage scientists claimed, noting that it was potentially performed to “make attribution tougher.”
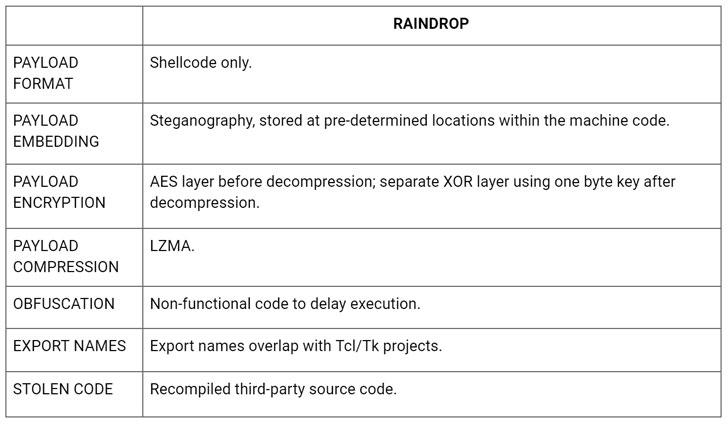
“While Teardrop was utilized on desktops that had been infected by the authentic Sunburst Trojan, Raindrop appeared elsewhere on the network, remaining utilised by the attackers to transfer laterally and deploy payloads on other desktops.”
It is really really worth noting that the attackers applied the Sunspot malware exclusively versus SolarWinds in September 2019 to compromise its develop setting and inject the Sunburst Trojan into its Orion network monitoring system. The tainted software was then delivered to 18,000 of the firm’s consumers.
Microsoft’s investigation of the Solorigate modus operandi last thirty day period discovered that the operators very carefully selected their targets, opting to escalate the attacks only in a handful of instances by deploying Teardrop based mostly on intel amassed for the duration of an original reconnaissance of the target environment for high-benefit accounts and belongings.
Now Raindrop (“bproxy.dll”) joins the combine. Although equally Teardrop and Raindrop act as a dropper for the Cobalt Strike Beacon, they also vary in a variety of means.
For a start out, Teardrop is shipped straight by the preliminary Sunburst backdoor, whereas Raindrop would seem to have been deployed with the goal of spreading across the victims’ network. What is actually additional, the malware reveals up on networks where by at least a single computer system has by now been compromised by Sunburst, with no indicator that Sunburst brought on its set up.
The two malware strains also use distinct packers and Cobalt Strike configurations.
Symantec did not discover the corporations impacted by Raindrop but stated the samples have been uncovered in a victim program that was jogging laptop or computer obtain and management software and on a device that was identified to execute PowerShell commands to infect further computer systems in the firm with the exact same malware.
Located this report intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to read more distinctive articles we submit.
Some sections of this report are sourced from:
thehackernews.com


 World Economic Forum: Action Required to Address Digital Inequalities Post-COVID
World Economic Forum: Action Required to Address Digital Inequalities Post-COVID