Cybersecurity researchers have uncovered new connections among a widely utilised pay back-for every-put in (PPI) malware company recognized as PrivateLoader and yet another PPI service dubbed ruzki.
“The threat actor ruzki (aka les0k, zhigalsz) advertises their PPI service on underground Russian-speaking discussion boards and their Telegram channels below the title ruzki or zhigalsz due to the fact at minimum May well 2021,” SEKOIA said.
The cybersecurity company reported its investigations into the twin solutions led it to conclude that PrivateLoader is the proprietary loader of the ruzki PPI malware support.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
PrivateLoader, as the title implies, functions as a C++-dependent loader to down load and deploy extra malicious payloads on contaminated Windows hosts. It truly is primarily dispersed via Seo-optimized internet sites that declare to deliver cracked computer software.
Though it was first documented earlier this February by Intel471, it is really reported to have been place to use starting off as early as Could 2021.

Some of the most popular commodity malware families propagated by way of PrivateLoader involve Redline Stealer, Socelars, Raccoon Stealer, Vidar, Tofsee, Amadey, DanaBot, and ransomware strains Djvu and End.
A May possibly 2022 assessment from Pattern Micro uncovered the malware distributing a framework referred to as NetDooka. A comply with-up report from BitSight late previous month identified major bacterial infections in India and Brazil as of July 2022.
A new alter spotted by SEKOIA is the use of VK.com paperwork service to host the destructive payloads as opposed to Discord, a change probable motivated by amplified checking of the platform’s material shipping and delivery network.
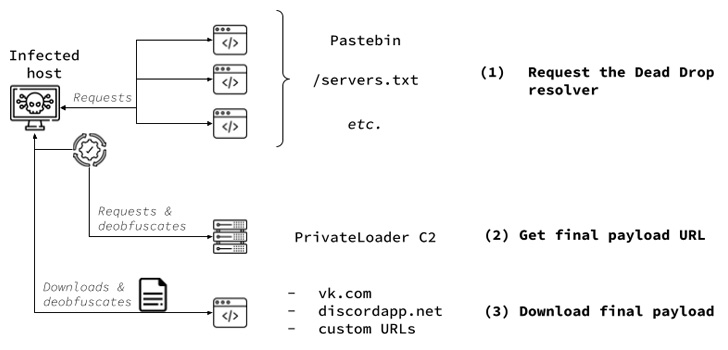
PrivateLoader is also configured to connect with command-and-regulate (C2) servers to fetch and exfiltrate information. As of mid-September, there are four active C2 servers, two in Russia and 1 every single in Czechia and Germany.
“Dependent on the broad assortment of malware households, which indicates a huge range of threat actors or intrusion sets running this malware, the PPI assistance running PrivateLoader is extremely desirable and well-known to attackers on underground marketplaces,” the researchers reported.
SEKOIA more said it unearthed ties amongst PrivateLoader and ruzki, a menace actor that sells bundles of 1,000 installations on contaminated programs located across the planet ($70), or precisely Europe ($300) or the U.S. ($1,000).
These advertisements, which have been positioned in the Lolz Guru cybercrime discussion board, goal risk actors (aka potential buyers) who wish to distribute their payloads through the PPI company.

The affiliation stems largely from the down below observations –
- An overlap in between the PrivateLoader C2 servers and that of URLs offered by ruzki to the subscribers so as to watch installation figures related to their strategies
- References to ruzki in PrivateLoader botnet sample names that ended up applied to provide the Redline Stealer, this sort of as ruzki9 and 3108_RUZKI, and
- The point that both of those PrivateLoader and ruzki commenced operations in Might 2021, with the ruzki operator making use of the time period “our loader” in Russian on its Telegram channel
“Spend-for every-Put in providers usually played a essential position in the distribution of commodity malware,” the researchers said.
“As yet yet another turnkey solution lowering the expense of entry into the cybercriminal market and a company contributing to a continuous professionalization of the cybercriminal ecosystem, it is extremely possible more PrivacyLoader-linked exercise will be observed in the limited term.”
Discovered this write-up interesting? Stick to THN on Fb, Twitter and LinkedIn to examine much more distinctive material we put up.
Some elements of this posting are sourced from:
thehackernews.com

 North Korean Hackers Spreading Trojanized Versions of PuTTY Client Application
North Korean Hackers Spreading Trojanized Versions of PuTTY Client Application