A new analysis of applications set to use by the Black Basta ransomware procedure has recognized ties involving the menace actor and the FIN7 (aka Carbanak) team.
This backlink “could suggest either that Black Basta and FIN7 retain a particular romantic relationship or that 1 or additional men and women belong to both teams,” cybersecurity firm SentinelOne explained in a specialized produce-up shared with The Hacker Information.
Black Basta, which emerged previously this 12 months, has been attributed to a ransomware spree that has claimed about 90 corporations as of September 2022, suggesting that the adversary is both of those perfectly-organized and very well-resourced.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
One noteworthy part that would make the group stand out, per SentinelOne, is the reality that there have been no symptoms of its operators trying to recruit affiliate marketers or advertising and marketing the malware as a RaaS on darknet discussion boards or crimeware marketplaces.
This has elevated the likelihood that the Black Basta developers possibly lower out affiliates from the chain and deploy the ransomware through their own tailor made toolset or alternatively operate with a shut set of affiliate marketers with no the need to marketplace their warez.
Attack chains involving Black Basta are recognized to leverage QBot (aka Qakbot), which, in change, is sent by usually means of phishing email messages that contains macro-centered Microsoft Office environment documents, with more recent infections using gain of ISO visuals and LNK droppers to get all-around Microsoft’s determination to block macros in files downloaded from the web by default.
Once Qakbot obtains a persistent foothold in the target natural environment, the Black Basta operator enters the scene to carry out reconnaissance by connecting to the target by way of the backdoor, adopted by exploiting regarded vulnerabilities (e.g., ZeroLogon, PrintNightmare, and NoPac) to escalate privileges.
Also place to use at this phase are backdoors this sort of as SystemBC (aka Coroxy) for facts exfiltration and the down load of extra malicious modules, prior to the conducting lateral motion and having techniques to impair defenses by disabling mounted security options.
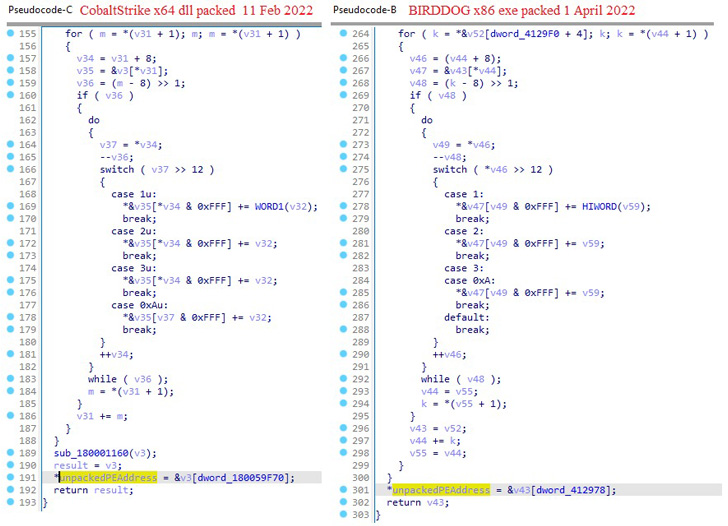
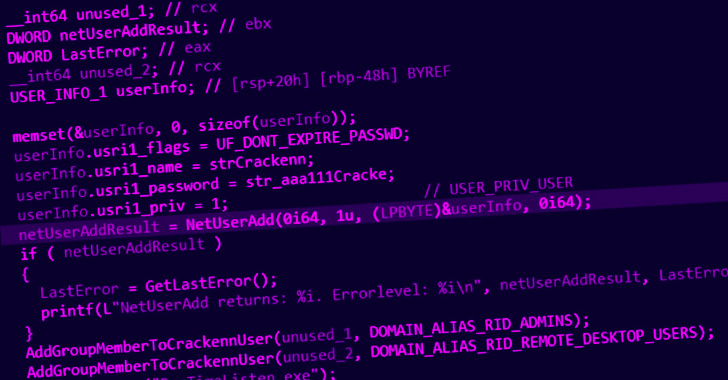
This also features a personalized EDR evasion resource that is been solely put to use in Black Basta incidents and will come embedded with a backdoor dubbed BIRDDOG, also termed as SocksBot and which has been utilized in many attacks earlier attributed to the FIN7 group.
The FIN7 cybercrime syndicate, lively since 2012, has a monitor document of mounting huge-scale malware campaigns focusing on the place-of-sale (PoS) programs aimed at the restaurant, gambling, and hospitality industries for economical fraud.

Around the previous two years, on the other hand, the group has switched to ransomware for illicitly making revenues, first as Darkside and then as BlackMatter and BlackCat, not to mention creating pretend front corporations to recruit unwitting penetration testers to phase ransomware attacks.
“At this issue, it is most likely that FIN7 or an affiliate started crafting applications from scratch in purchase to disassociate their new functions from the previous,” scientists Antonio Cocomazzi and Antonio Pirozzi stated. “It is probably that the developer(s) at the rear of their instruments to impair target defenses is, or was, a developer for FIN7.”
The conclusions arrive months right after the Black Basta actor was observed utilizing the Qakbot trojan to deploy Cobalt Strike and Brute Ratel C4 frameworks as a second-phase payload in modern attacks.
“The crimeware ecosystem is regularly increasing, altering, and evolving,” the scientists concluded. “FIN7 (or Carbanak) is frequently credited with innovating in the criminal area, getting attacks against banking companies and PoS programs to new heights past the strategies of their friends.”
The disclosure also arrives as the U.S. Money Crimes Enforcement Network (FinCEN) noted a surge in ransomware attacks focusing on domestic entities from 487 in 2020 to 1,489 in 2021, incurring a full price of $1.2 billion, a 188% soar from $416 million the past yr.
Found this posting exciting? Abide by THN on Facebook, Twitter and LinkedIn to go through far more distinctive written content we write-up.
Some components of this report are sourced from:
thehackernews.com

 TikTok Confirms Chinese Staff Can Access UK and EU User Data
TikTok Confirms Chinese Staff Can Access UK and EU User Data