Cybersecurity scientists, for the 1st time, may have found a potential link involving the backdoor made use of in the SolarWinds hack to a earlier identified malware pressure.
In new investigation posted by Kaspersky researchers currently, the cybersecurity business reported it found out a number of options that overlap with another backdoor known as Kazuar, a .NET-based mostly malware initial documented by Palo Alto Networks in 2017.
Disclosed early past month, the espionage campaign was notable for its scale and stealth, with the attackers leveraging the believe in affiliated with SolarWinds Orion program to infiltrate govt companies and other providers so as to deploy a customized malware codenamed “Sunburst.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Shared Features Among Sunburst and Kazuar
Attribution for the SolarWinds offer-chain compromise has been difficult in aspect owing to minimal-to-no clues linking the attack infrastructure to past strategies or other effectively-regarded menace groups.
But Kaspersky’s most up-to-date evaluation of the Sunburst backdoor has unveiled a variety of shared functions among the malware and Kazuar, main the scientists to suspect that —
- The two Sunburst and Kazuar had been developed by the very same risk team
- The adversary behind Sunburst utilized Kazuar as an inspiration
- The teams guiding Kazuar (Turla) and Sunburst (UNC2452 or Dark Halo) attained the malware from a single supply
- The developers of Kazuar moved to yet another group, taking their toolset with them, or
- The Sunburst developers deliberately launched these links as “wrong flag” to change blame to a different team
The commonalities shared in between the two malware households incorporate the use of a sleeping algorithm to continue to be dormant for a random period of time in between connections to a C2 server, the comprehensive use of the FNV-1a hash to obfuscate the malicious code, and the use of a hashing algorithm to crank out special target identifiers.
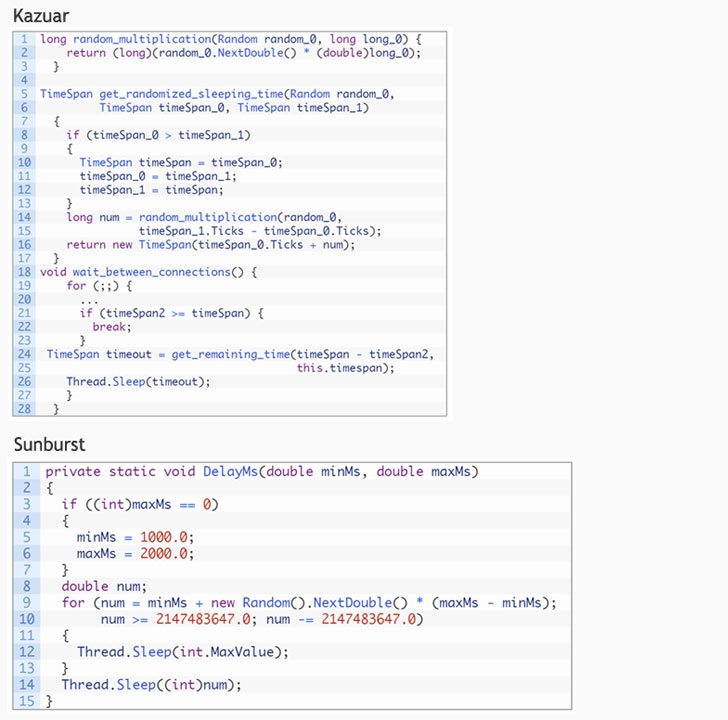
Even though Kazuar randomly selects a sleeping interval involving two and 4 weeks concerning C2 connections, Sunburst randomly opts for a sleeping time period concerning 12 and 14 days before making contact with the server for original reconnaissance. But researchers famous that the components made use of to determine the sleeping time stays the exact same.
Kazuar’ Feasible Hyperlinks to Turla
Kazuar is a absolutely highlighted backdoor created making use of the .NET Framework and depends on a command-and-command (C2) channel to let actors to interact with the compromised method and exfiltrate facts. Its characteristics run the regular adware gamut, with aid for running malicious instructions, capture screenshots, and even deploy added functionalities by using a plugin command.
Palo Alto Networks’ Device 42 staff tentatively joined the tool to the Russian danger group Turla (aka Uroburos and Snake) dependent on the reality that the “code lineage in Kazuar can be traced again to at least 2005.”
What is much more, on November 18, 2020, Kazuar seems to have been through a complete redesign with a new keylogger and password-stealing features added to the backdoor that is carried out in the variety of C2 server command.
Though it is really standard for threat actors to retain updating their toolset and introduce options created to bypass endpoint detection and response (EDR) systems, Kaspersky scientists lifted the risk that the alterations may have been released in response to the SolarWinds breach.
“Suspecting the SolarWinds attack could possibly be found out, the Kazuar code was modified to resemble the Sunburst backdoor as very little as achievable,” the researchers claimed.
CISA Updates SolarWinds Advisory
Very last 7 days, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), together with the Federal Bureau of Investigation (FBI), the Business office of the Director of National Intelligence (ODNI), and the Nationwide Security Company (NSA), issued a joint assertion formally accusing an adversary “most likely Russian in origin” for staging the SolarWinds hack.
Moreover, CISA, in an update to its advisory on January 6, said, “incident response investigations have recognized that preliminary obtain in some scenarios was received by password guessing, password spraying, and inappropriately secured administrative qualifications obtainable by way of exterior distant accessibility expert services.”
“These code overlaps involving Kazuar and Sunburst are exciting and represent the 1st potential discovered backlink to a earlier known malware family members,” Kaspersky scientists concluded.
“Whilst Kazuar and Sunburst might be relevant, the nature of this relation is however not very clear. Via even further analysis, it is achievable that proof confirming a person or several of these details may come up. At the similar time, it is also doable that the Sunburst builders were being genuinely great at their opsec and failed to make any blunders, with this connection being an elaborate fake flag.”
Found this article intriguing? Observe THN on Facebook, Twitter and LinkedIn to study a lot more exceptional content we article.
Some parts of this short article are sourced from:
thehackernews.com


 What is zero trust?
What is zero trust?