An unidentified advanced persistent danger (APT) group has been linked to a series of spear-phishing attacks focusing on Russian authorities entities since the onset of the Russo-Ukrainian war in late February 2022.
“The campaigns […] are created to implant a Distant Entry Trojan (RAT) that can be made use of to surveil the personal computers it infects, and operate commands on them remotely,” Malwarebytes mentioned in a complex report printed Tuesday.
The cybersecurity corporation attributed the attacks with reduced self-confidence to a Chinese hacking team, citing infrastructure overlaps involving RAT and Sakula Rat malware employed by a danger actor identified as Deep Panda.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attack chains, while leveraging distinct lures about the training course of two months, all utilized the identical malware barring little distinctions in the resource code.

The marketing campaign is said to have commenced all over February 26, days right after Russia’s navy invasion of Ukraine, with the e-mail distributing the RAT less than the guise of an interactive map of Ukraine (“interactive_map_UA.exe”).
The development once once more demonstrates menace actors’ abilities to adapt and alter their attacks to earth gatherings, utilizing the most suitable and up-to-day lures to optimize their probabilities of achievements.
A second early March attack wave primarily targeted the condition-controlled RT Television and involved the use of a rogue software take care of for the Log4Shell vulnerability that created headlines in late 2021.
In addition to which includes the patch in the form of a compressed TAR file, the email concept also came with a PDF document with guidance to install the patch and shown the greatest security practices to observe, together with enabling two-factor authentication, employing Kaspersky antivirus, and refraining from opening or replying to suspicious emails.
In a further try to raise the legitimacy of the email, the document also contained a VirusTotal URL pointing to an unrelated file to give the effect that the Log4j patch file is not destructive.
What’s far more, the email showcased back links to an attacker-controlled area “rostec[.]digital” together with fraudulent profiles established on Fb and Instagram alluding to the Russian defense conglomerate.

“Curiously, the danger actor established the Fb website page in June 2021, nine months before it was utilised in this campaign,” the scientists claimed. “This was likely an endeavor to draw in followers, to make the page seem additional authentic, and it suggests the APT team ended up planning this campaign lengthy prior to the invasion of Ukraine.”
The 3rd iteration of the attack that followed produced use of yet another destructive executable file — this time “make_rosteh4.exe” — in an try to go off the malware as nevertheless it can be from Rostec.
Lastly, in mid-April 2022, the attackers pivoted to a career-themed phishing bait for Saudi Aramco, a Saudi Arabian petroleum and natural gasoline corporation, the weaponized Microsoft Phrase document performing as a result in for an an infection sequence to deploy the RAT.
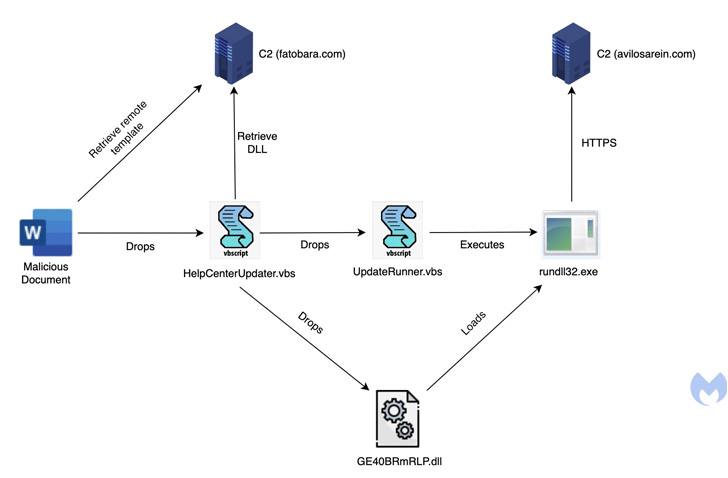
The DLL payload employs a range of state-of-the-art tips to thwart analysis, together with management circulation flattening and string obfuscation, even though also incorporating capabilities that enable it to arbitrary documents despatched from a distant server to the contaminated host and execute command-line directions.
The results closely stick to conclusions from Examine Issue that a Chinese adversarial collective with connections to Stone Panda and Mustang Panda specific at minimum two investigate institutes located in Russia with a previously undocumented backdoor referred to as Spinner.
Found this post interesting? Adhere to THN on Facebook, Twitter and LinkedIn to read through far more special content material we put up.
Some sections of this posting are sourced from:
thehackernews.com


 [Template] Incident Response for Management Presentation
[Template] Incident Response for Management Presentation