At least a few alleged hacktivist teams doing the job in aid of Russian pursuits are possible executing so in collaboration with state-sponsored cyber risk actors, in accordance to Mandiant.
The Google-owned danger intelligence and incident reaction agency reported with moderate self confidence that “moderators of the purported hacktivist Telegram channels ‘XakNet Workforce,”https://thehackernews.com/2022/09/”Infoccentr,’ and ‘CyberArmyofRussia_Reborn’ are coordinating their functions with Russian Main Intelligence Directorate (GRU)-sponsored cyber danger actors.”
Mandiant’s evaluation is based mostly on proof that the leakage of facts stolen from Ukrainian corporations happened within 24 hours of malicious wiper incidents undertaken by the Russian nation-condition group tracked as APT28 (aka Extravagant Bear, Sofacy, or Strontium).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

To that conclusion, 4 of the 16 info leaks from these teams coincided with disk wiping malware attacks by APT28 that included the use of a pressure dubbed CaddyWiper.
APT28, active considering the fact that at minimum 2009, is linked with the Russian army intelligence agency, the Standard Team Principal Intelligence Directorate (GRU), and drew community focus in 2016 for the breaches of the Democratic Nationwide Committee (DNC) in the operate-up to the U.S. presidential election.
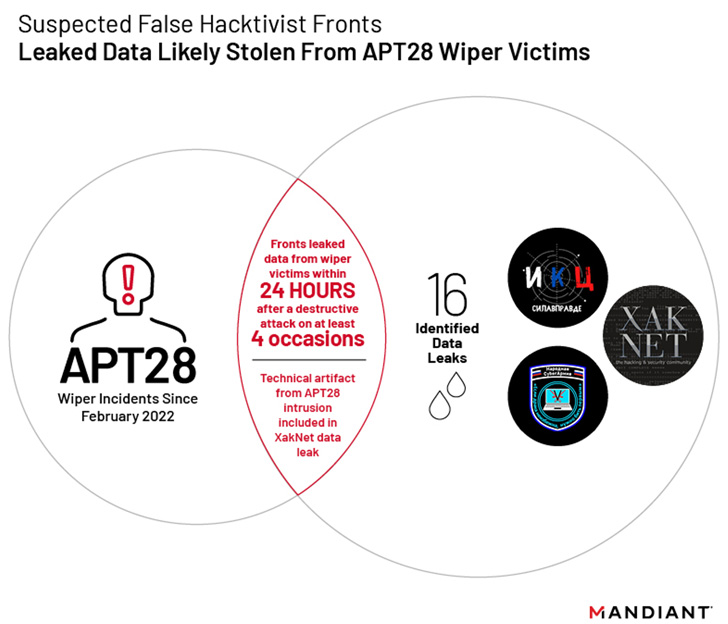
While the so-identified as hacktivist teams have performed distributed denial-of-provider (DDoS) attacks and internet site defacements to focus on Ukraine, indications are that these phony personas are a front for facts operations and harmful cyber pursuits.
That said, the correct mother nature of the connection and the degree of affiliation with the Russian condition continues to be mysterious, while it implies both immediate involvement from GRU officers on their own or by way of the moderators operating the Telegram channels.

This line of reasoning is substantiated by XakNet’s leak of a “unique” complex artifact that APT28 used in its compromise of a Ukrainian network and the actuality that CyberArmyofRussia_Reborn’s data releases are preceded by APT28 intrusion functions.
The cybersecurity enterprise pointed out it also unearthed some degree of coordination amongst the XakNet Crew and Infoccentr as very well as the pro-Russia group KillNet.
“The war in Ukraine has also introduced novel options to recognize the totality, coordination, and success of Russia cyber systems, which include the use of social media platforms by threat actors,” Mandiant reported.
Located this article exciting? Adhere to THN on Facebook, Twitter and LinkedIn to read a lot more distinctive articles we publish.
Some parts of this write-up are sourced from:
thehackernews.com


 Australia looks to amend privacy rules following Optus data breach
Australia looks to amend privacy rules following Optus data breach