Details have emerged about a now-patched security flaw in Windows Typical Log File Method (CLFS) that could be exploited by an attacker to achieve elevated permissions on compromised machines.
Tracked as CVE-2022-37969 (CVSS score: 7.8), the issue was resolved by Microsoft as element of its Patch Tuesday updates for September 2022, when also noting that it was getting actively exploited in the wild.
“An attacker ought to by now have accessibility and the capacity to run code on the target technique,” the business pointed out in its advisory. “This method does not make it possible for for distant code execution in scenarios the place the attacker does not already have that capacity on the concentrate on program.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It also credited researchers from CrowdStrike, DBAPPSecurity, Mandiant, and Zscaler for reporting the vulnerability without delving into supplemental particulars encompassing the mother nature of the attacks.

Now, the Zscaler ThreatLabz researcher team has disclosed that it captured an in-the-wild exploit for the then zero-day on September 2, 2022.
“The trigger of the vulnerability is thanks to the absence of a rigid bounds check on the field cbSymbolZone in the Foundation Document Header for the base log file (BLF) in CLFS.sys,” the cybersecurity business reported in a root lead to analysis shared with The Hacker News.
“If the discipline cbSymbolZone is set to an invalid offset, an out-of-bounds create will manifest at the invalid offset.”
CLFS is a typical-goal logging assistance that can be made use of by computer software apps working in each person-manner or kernel-method to report data as perfectly as functions and enhance log access.
Some of the use circumstances involved with CLFS include things like on the net transaction processing (OLTP), network gatherings logging, compliance audits, and threat evaluation.
According to Zscaler, the vulnerability is rooted in a metadata block known as foundation report that is existing in a base log file, which is produced when a log file is produced working with the CreateLogFile() function.

“[Base record] has the image tables that retail outlet data on the numerous customer, container and security contexts associated with the Foundation Log File, as properly as accounting info on these,” in accordance to Alex Ionescu, main architect at Crowdstrike.
As a final result, a profitable exploitation of CVE-2022-37969 by way of a specifically crafted base log file could lead to memory corruption, and by extension, induce a method crash (aka blue screen of death or BSoD) in a reliable manner.
That stated, a system crash is just a single of the outcomes that occurs out of leveraging the vulnerability, for it could also be weaponized to achieve privilege escalation.
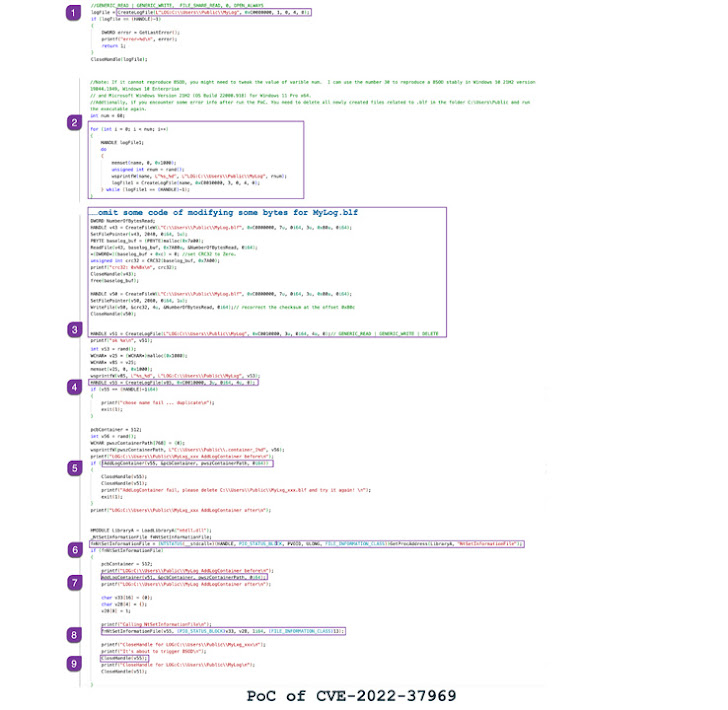
Zscaler has additional manufactured offered proof-of-notion (PoC) directions to trigger the security hole, producing it critical that customers of Windows up grade to the most recent variation to mitigate likely threats.
Observed this post exciting? Abide by THN on Facebook, Twitter and LinkedIn to examine much more unique content material we put up.
Some elements of this posting are sourced from:
thehackernews.com


 Mirai Botnet Targeted Wynncraft Minecraft Server, Cloudflare Reports
Mirai Botnet Targeted Wynncraft Minecraft Server, Cloudflare Reports