An Iranian threat actor has unleashed a new cyberespionage marketing campaign towards a achievable Lebanese goal with a backdoor able of exfiltrating delicate information from compromised methods.
Cybersecurity agency Verify Issue attributed the procedure to APT34, citing similarities with prior procedures utilised by the risk actor as well as dependent on its sample of victimology.
APT34 (aka OilRig) is acknowledged for its reconnaissance strategies aligned with the strategic passions of Iran, principally hitting financial, federal government, vitality, chemical, and telecommunications industries in the Center East.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The group normally resorts to focusing on folks by the use of booby-trapped job supply files, shipped right to the victims by way of LinkedIn messages, and the newest marketing campaign is no exception, despite the fact that the method of delivery remains unclear as yet.
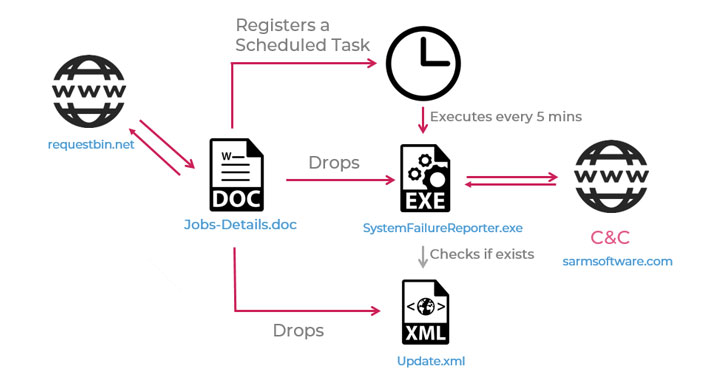
The Term doc analyzed by Test Stage — which was uploaded to VirusTotal from Lebanon on January 10 — promises to offer information about various positions at a U.S.-based mostly consulting firm named Ntiva IT, only to trigger the an infection chain upon activating the embedded destructive macros, eventually resulting in the deployment of a backdoor called “SideTwist.”

Aside from gathering simple information and facts about the victim’s equipment, the backdoor establishes connections with a remote server to await additional commands that enable it to down load files from the server, add arbitrary data files, and execute shell commands, the success of which are posted again to the server.
Look at Place notes that the use of new backdoor details to the group’s ongoing initiatives to overhaul and update their payload arsenal in the wake of a 2019 leak of its hacking applications, which also doxxed many officers of the Iranian Ministry of Intelligence who were being concerned with APT34 functions.
“Iran backed APT34 exhibits no sign of slowing down, further more pushing its political agenda in the center-east, with an ongoing target on Lebanon — employing offensive cyber operations,” the scientists said. “Even though protecting its modus operandi and reusing previous procedures, the team carries on to create new and up to date resources to limit the feasible detection of their tools by security sellers.”
Located this post appealing? Stick to THN on Fb, Twitter and LinkedIn to study more exclusive content we write-up.
Some areas of this article are sourced from:
thehackernews.com

 Online Fraud in the UK Up 179% in the Last Decade
Online Fraud in the UK Up 179% in the Last Decade