A new covert attack campaign singled out various military services and weapons contractor providers with spear-phishing e-mail to induce a multi-phase an infection approach made to deploy an unfamiliar payload on compromised devices.
The really-qualified intrusions, dubbed STEEP#MAVERICK by Securonix, also targeted a strategic supplier to the F-35 Lightning II fighter aircraft.
“The attack was carried out commencing in late summer time 2022 concentrating on at minimum two large-profile army contractor companies,” Den Iuzvyk, Tim Peck, and Oleg Kolesnikov reported in an assessment.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Infection chains start off with a phishing mail with a ZIP archive attachment that contains a shortcut file that promises to be a PDF doc about “Organization & Rewards,” which is then employed to retrieve a stager — an first binary which is utilized to down load the preferred malware — from a remote server.
This PowerShell stager sets the stage for a “robust chain of stagers” that progresses by way of seven far more actions, when the remaining PowerShell script executes a distant payload “header.png” hosted on a server named “terma[.]application.”
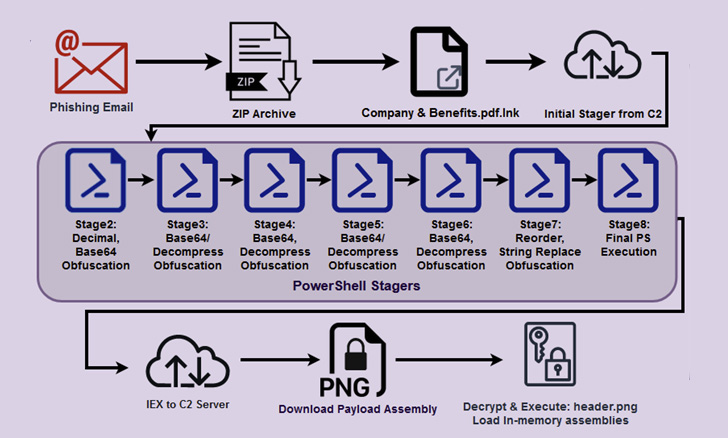
“When we have been capable to download and evaluate the header.png file, we were not in a position to decode it as we believe that the marketing campaign was concluded and our principle is that the file was replaced in buy to reduce even more evaluation,” the researchers discussed.
“Our tries to decode the payload would only create garbage facts.”
What is actually notable about the modus operandi is the incorporation of obfuscated code built to thwart investigation, in addition to scanning for the existence of debugging application and halt the execution if the process language is set to Chinese or Russian.
The malware is also created to verify the amount of money of actual physical memory, and when again terminate itself if it can be less than 4GB. Also involved is a verify for virtualization infrastructure to decide if the malware is currently being executed in an evaluation natural environment or sandbox.

But if this exam fails, somewhat than merely quitting the execution, the malware disables system network adapters, reconfigures Windows Firewall to block all inbound and outbound website traffic, recursively deletes knowledge in all drives, and shuts down the pc.
Need to all these checks move, the PowerShell stager proceeds to disable logging, insert Windows Defender exclusions for LNK, RAR, and EXE files, and establish persistence via a scheduled process or Windows Registry modifications.
“General, it is distinct that this attack was relatively innovative with the malicious menace actor paying precise attention to opsec,” the scientists pointed out. “Whilst this was a extremely targeted attack, the tactics and tactics utilized are nicely identified and it is essential to stay vigilant.”
Located this write-up attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to go through additional distinctive content we post.
Some areas of this short article are sourced from:
thehackernews.com

 Five Steps to Mitigate the Risk of Credential Exposure
Five Steps to Mitigate the Risk of Credential Exposure