An Android spyware application has been spotted masquerading as a “Method Supervisor” provider to stealthily siphon sensitive info saved in the contaminated products.
Interestingly, the app — that has the deal title “com.remote.application” — establishes get in touch with with a distant command-and-regulate server, 82.146.35[.]240, which has been formerly discovered as infrastructure belonging to the Russia-based mostly hacking team acknowledged as Turla.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
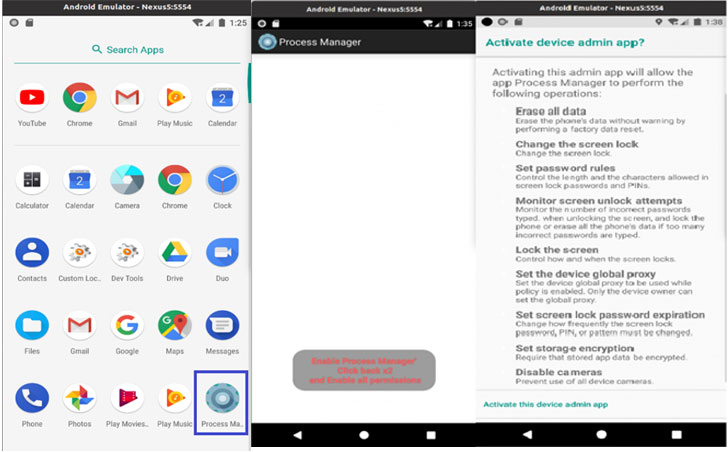
“When the software is operate, a warning seems about the permissions granted to the application,” Lab52 researchers claimed. “These contain display unlock attempts, lock the screen, set the unit world proxy, set display screen lock password expiration, established storage encryption and disable cameras.”
The moment the app is “activated,” the malware gets rid of its equipment-shaped icon from the household monitor and runs in the qualifications, abusing its large permissions to entry the device’s contacts and contact logs, observe its locale, ship and read through messages, accessibility exterior storage, snap images, and document audio.
The collected data is captured in a JSON format and subsequently transmitted to the aforementioned remote server. Inspite of the overlap in the C2 server utilized, Lab52 reported it isn’t going to have ample evidence to attribute the malware to the Turla group.
Also unknown at this phase is the precise initial entry vector used for distributing the adware and supposed targets of the marketing campaign.
That explained, the rogue Android app also tries to download a respectable application identified as Roz Dhan (indicating “Daily Wealth” in Hindi) that has around 10 million installations and lets people to gain cash rewards for completing surveys and questionnaires.
“The software, [which] is on Google Enjoy and is utilized to earn dollars, has a referral system that is abused by the malware,” the scientists explained. “The attacker installs it on the gadget and can make a revenue.”
Observed this posting attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to read through a lot more exclusive content material we article.
Some elements of this write-up are sourced from:
thehackernews.com




 Multiple Hacker Groups Capitalizing on Ukraine Conflict for Distributing Malware
Multiple Hacker Groups Capitalizing on Ukraine Conflict for Distributing Malware