A shellcode-centered packer dubbed TrickGate has been efficiently running devoid of attracting notice for more than 6 a long time, while enabling risk actors to deploy a wide array of malware these types of as TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil about the a long time.
“TrickGate managed to continue to be underneath the radar for several years because it is transformative – it undergoes adjustments periodically,” Look at Level Research’s Arie Olshtein said, contacting it a “master of disguises.”
Presented as a assistance to other menace actors considering that at the very least late 2016, TrickGate assists conceal payloads driving a layer of wrapper code in an endeavor to get previous security options mounted on a host. Packers can also function as crypters by encrypting the malware as an obfuscation mechanism.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Packers have diverse characteristics that let them to circumvent detection mechanisms by showing as benign data files, getting tough to reverse engineer, or incorporating sandbox evasion tactics,” Proofpoint famous in December 2020.
But the regular updates to the commercial packer-as-a-support meant TrickGate has been tracked less than various names such as new loader, Loncom, and NSIS-based crypter considering the fact that 2019.
Telemetry knowledge gathered by Check Issue indicates that the danger actors leveraging TrickGate have mostly singled out the producing sector, and to a lesser extent, education, healthcare, authorities, and finance verticals.
The most common malware households utilised in the attacks in the previous two months include FormBook, LokiBot, Agent Tesla, Remcos, and Nanocore, with important concentrations documented in Taiwan, Turkey, Germany, Russia, and China.
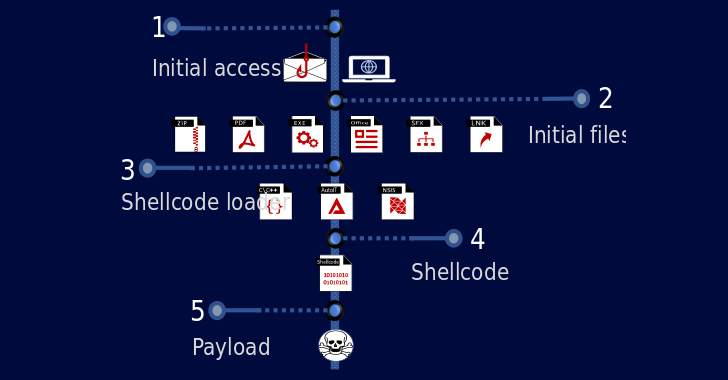
The an infection chain consists of sending phishing emails with malicious attachments or booby-trapped back links that direct to the obtain of a shellcode loader which is liable for decrypting and launching the actual payload into memory.
The Israeli cybersecurity firm’s investigation of the shellcode demonstrates that it “has been consistently up to date, but the key functionalities exist on all the samples because 2016,” Olshtein famous. “The injection module has been the most regular component over the a long time and has been observed in all TrickGate shellcodes.”
Located this posting fascinating? Observe us on Twitter and LinkedIn to go through more unique content we article.
Some areas of this write-up are sourced from:
thehackernews.com


 Killnet Attackers DDoS US and Dutch Hospitals
Killnet Attackers DDoS US and Dutch Hospitals