In nonetheless a different signal that Telegram is more and more turning into a thriving hub for cybercrime, researchers have discovered that threat actors are utilizing the messaging system to peddle phishing kits and aid set up phishing strategies.
“To boost their ‘goods,’ phishers build Telegram channels by way of which they teach their viewers about phishing and entertain subscribers with polls like, ‘What type of own knowledge do you desire?’,” Kaspersky web written content analyst Olga Svistunova mentioned in a report posted this 7 days.
The links to these Telegram channels are distributed via YouTube, GitHub, and the phishing kits that are developed by the crooks on their own. The Russian cybersecurity firm mentioned it detected about 2.5 million malicious URLs generated working with phishing kits in the past 6 months.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
One particular of the distinguished providers available is to present menace actors with Telegram bots that automate the process of building phishing web pages and accumulating consumer data.
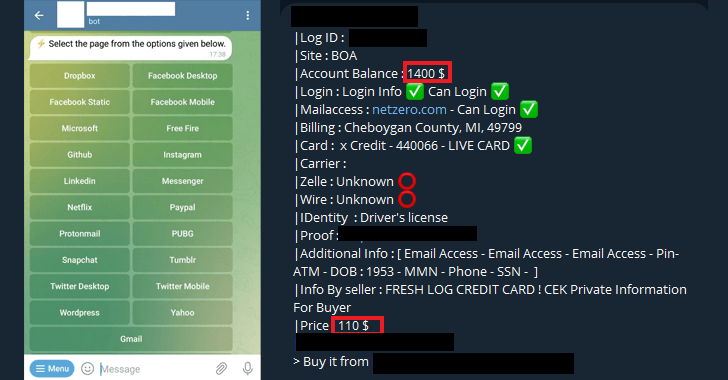
While it is really the scammer’s duty to distribute the pretend login internet pages to targets of interest, the credentials captured in these web pages are despatched again by suggests of an additional Telegram bot.
Other bot solutions go a phase even more by advertising and marketing selections to deliver phishing webpages that mimic a genuine services, which are then applied to lure potential victims below the pretext of giving away no cost likes on social media expert services.
“Scammer-operated Telegram channels occasionally post what appears to be exceptionally generous features, for illustration, zipped up sets of ready-to-use phishing kits that target a massive variety of world wide and community makes,” Svistunova stated.
In some conditions, phishers have also been observed sharing users’ own knowledge with other subscribers for free in hopes of attracting aspiring criminals, only to offer paid kits to people who want to pull off much more these types of attacks. The scammers further more supply to teach “how to phish for severe dollars.”
Using absolutely free propositions is also a way for scammers to trick hard cash-strapped and novice criminals into working with their phishing kits, resulting in double theft, where the stolen information is also sent to the creator without their awareness.
Paid solutions, on the other hand, include things like sophisticated kits that boast of an pleasing style and design and capabilities like anti-bot detection, URL encryption and geoblocking that danger actors could use to commit extra advanced social engineering schemes. These types of web pages expense everywhere concerning $10 to $280.
Another paid out category involves the sale of individual facts, with credentials of lender accounts marketed at various premiums primarily based on the harmony. For illustration, an account with a balance of $49,000 was place up for $700.
What is actually far more, phishing services are promoted by way of Telegram on a membership foundation (i.e., phishing-as-a-support or PhaaS), whereby the developers rent the kits for a monthly charge in return for giving normal updates.
Upcoming WEBINARLearn to Protected the Identity Perimeter – Tested Approaches
Boost your enterprise security with our approaching professional-led cybersecurity webinar: Explore Identification Perimeter strategies!
Never Overlook Out – Preserve Your Seat!
Also promoted as a membership is a 1-time password (OTP) bot that phone calls users and convinces them to enter the two-factor authentication code on their phones to assist bypass account protections.
Location up these expert services are somewhat clear-cut. What is extra tough is earning the believe in and loyalty of the shoppers. And some suppliers go out of their way to assure that all the info is encrypted so that no 3rd-events, including by themselves, can browse it.
The conclusions also adhere to an advisory from Cofense earlier this January, which uncovered an 800% raise 12 months-around-calendar year in the use of Telegram bots as exfiltration destinations for phished data.
“Wannabe phishers utilised to have to have to obtain a way on to the dark web, review the message boards there, and do other factors to get started out,” Svistunova stated. “The threshold to joining the phisher group decreased at the time malicious actors migrated to Telegram and now share insights and awareness, usually for absolutely free, correct there in the well-liked messaging service.”
Identified this post interesting? Abide by us on Twitter and LinkedIn to go through a lot more distinctive information we article.
Some elements of this write-up are sourced from:
thehackernews.com

 What is the Network and Information Security 2 (NIS2) Directive?
What is the Network and Information Security 2 (NIS2) Directive?