A new set of critical vulnerabilities has been disclosed in the Realtek RTL8170C Wi-Fi module that an adversary could abuse to achieve elevated privileges on a machine and hijack wireless communications.
“Productive exploitation would direct to complete handle of the Wi-Fi module and potential root obtain on the OS (these as Linux or Android) of the embedded unit that utilizes this module,” researchers from Israeli IoT security business Vdoo stated in a generate-up released yesterday.
The Realtek RTL8710C Wi-Fi SoC underpins Ameba, an Arduino-compatible programmable system outfitted with peripheral interfaces for creating a assortment of IoT apps by products spanning across agriculture, automotive, strength, healthcare, industrial, security, and wise house sectors.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The flaws influence all embedded and IoT equipment that use the element to hook up to Wi-Fi networks and would involve an attacker to be on the same Wi-Fi network as the equipment that use the RTL8710C module or know the network’s pre-shared essential (PSK), which, as the title indicates, is a cryptographic mystery employed to authenticate wireless consumers on nearby spot networks.
The findings stick to an previously analysis in February that observed similar weaknesses in the Realtek RTL8195A Wi-Fi module, main among them becoming a buffer overflow vulnerability (CVE-2020-9395) that permits an attacker in the proximity of an RTL8195 module to fully get about the module with no getting to know the Wi-Fi network password.
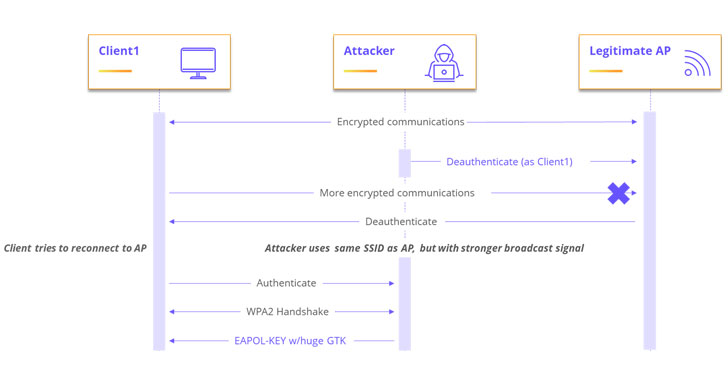
In the identical vein, the RTL8170C Wi-Fi module’s WPA2 four-way handshake mechanism is vulnerable to two stack-dependent buffer overflow vulnerabilities (CVE-2020-27301 and CVE-2020-27302, CVSS scores: 8.) that abuse the attacker’s information of the PSK to obtain distant code execution on WPA2 clientele that use this Wi-Fi module.
As a possible authentic-planet attack scenario, the scientists shown a proof-of-notion (PoC) exploit wherein the attacker masquerades as a respectable accessibility level and sends a malicious encrypted group temporal important (GTK) to any client (aka supplicant) that connects to it via WPA2 protocol. A team temporal crucial is utilized to protected all multicast and broadcast targeted traffic.
Vdoo reported there are no acknowledged attacks underway exploiting the vulnerabilities, adding firmware variations introduced soon after Jan. 11, 2021 include things like mitigations that resolve the issue. The company also recommends utilizing a “solid, private WPA2 passphrase” to stop exploitation of the above issues in scenarios the place the device’s firmware are unable to be current.
Discovered this report exciting? Stick to THN on Fb, Twitter and LinkedIn to go through a lot more exceptional material we article.
Some pieces of this article are sourced from:
thehackernews.com

 Weekly threat roundup: Froala, WordPress, Siemens
Weekly threat roundup: Froala, WordPress, Siemens