A nascent Go-centered malware recognized as Aurora Stealer is being progressively deployed as element of campaigns built to steal sensitive facts from compromised hosts.
“These infection chains leveraged phishing internet pages impersonating down load web pages of reputable software package, such as cryptocurrency wallets or distant obtain resources, and the 911 technique creating use of YouTube movies and Search engine optimization-poised fake cracked program download websites,” cybersecurity organization SEKOIA said.
Initial marketed on Russian cybercrime community forums in April 2022, Aurora was offered as a commodity malware for other danger actors, describing it as a “multi-purpose botnet with thieving, downloading and distant accessibility abilities.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
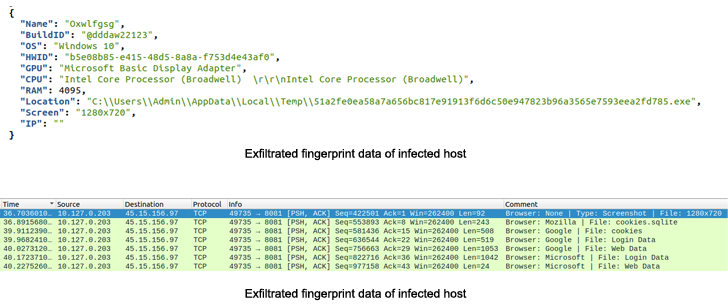
In the intervening months, the malware has been scaled down to a stealer that can harvest data files of desire, knowledge from 40 cryptocurrency wallets, and applications like Telegram.
Aurora also will come with a loader that can deploy a next-phase payloading making use of a PowerShell command.
The cybersecurity enterprise reported at least diverse cybercrime teams, named traffers, who are dependable for redirecting user’s traffic to malicious information operated by other actors, have added Aurora to their toolset, either completely or alongside RedLine and Raccoon.
“Aurora is another infostealer concentrating on data from browsers, cryptocurrency wallets, regional systems, and performing as a loader,” SEKOIA mentioned. “Sold at a significant value on industry destinations, collected info is of unique curiosity to cybercriminals, permitting them to have out stick to-up rewarding campaigns, together with Massive Sport Looking operations.”
The progress also will come as researchers from Palo Alto Networks Unit 42 thorough an enhanced model of a further stealer named Typhon Stealer.
The new variant, dubbed Typhon Reborn, is made to steal from cryptocurrency wallets, web browsers, and other system info, while removing earlier present features like keylogging and cryptocurrency mining in a possible attempt to reduce detection.
“Typhon Stealer provided menace actors with an effortless to use, configurable builder for retain the services of,” Unit 42 scientists Riley Porter and Uday Pratap Singh explained.
“Typhon Reborn’s new anti-assessment tactics are evolving along industry lines, starting to be more helpful in the evasion practices although broadening their toolset for stealing victim data.”
Found this post appealing? Stick to THN on Facebook, Twitter and LinkedIn to read extra exceptional written content we post.
Some components of this posting are sourced from:
thehackernews.com


 Here’s How to Ensure Your Incident Response Strategy is Ready for Holiday Hackers
Here’s How to Ensure Your Incident Response Strategy is Ready for Holiday Hackers