Shutterstock
Security researchers have noticed a significant raise in the variety of attacks against Zoho software program, with a number of scenarios and organisations by now influenced throughout the world.
A complete of 13 organisations across industries such as defence, strength, technology source chain, health care, and schooling have been compromised above a a few-thirty day period period of time, according to Palo Alto Networks’ Unit 42.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Thriving exploitation of the program flaws can lead to remote code execution (RCE) and provide attacks using administrator privileges.
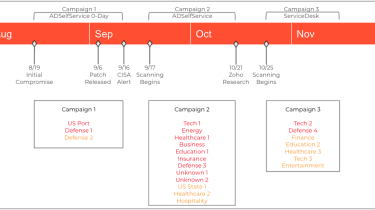
Attacks began back in September when CISA warned of cyber criminals exploiting a recently identified, critical-rated vulnerability, tracked as CVE-2021-40539, in ManageEngine ADSelfService Additionally, a self-service password administration and solitary indication-on option product from Zoho.
Zoho issued a patch for the exploit in September, followed by an advisory on 22 November conveying the severity of the issue to customers and urging them to patch their programs.
Nonetheless, scientists at Unit 42 drew interest to a 2nd campaign focusing on a various Zoho product in November. The exploit tracked as CVE-2021-44077 which affects ManageEngine ServiceDesk Moreover, a assist desk and asset management product or service, was a lot more complex and challenging to detect, researchers observed.
Unit 42 researchers determined that 47% of ADSelfService Additionally and 62% of ADServiceDesk Additionally cases across the world are even now applying vulnerable variations and have but to be patched by prospects.
The most new results from the past two months have verified an supplemental four businesses compromised utilizing the vulnerabilities, two in ADSelfService Plus and two in ServiceDesk In addition, bringing the full to 13 immediately after an preliminary 9 cases were confirmed.
Researchers stated they hadn’t recognized any publicly obtainable proof of idea code for the exploit but noticed that the group guiding the attacks was certainly utilizing just one of their own exploits to compromise unpatched variations of the software program.
The team utilized a range of preliminary entry vectors to breach Zoho’s infrastructure, letting them to drop a Godzilla webshell using RCE to deliver the group with supplemental entry and persistence in compromised units.
Zoho solution attack timeline
Palo Alto Networks Device 42
Two requests were despatched to the Rest API allowing the attackers to add the msiexec.exe executable and start the destructive payload.
Godzilla was utilized in attacks on both ADSelfService Furthermore and ADServiceDesk In addition, but utilised various files. A Java Server Web pages (JSP) file was utilized with ADSelfService Additionally but Godzilla was dropped utilizing an Apache Tomcat Java Servlet Filter with ADServiceDesk Plus.
Employing a filter permitted attackers to sift inbound and outbound requests to determine which were intended for the webshell. Setting up Godzilla as a webshell also intended that there was no unique URL utilised by the group to deliver its requests to the webshell, and it could also bypass a ADServiceDesk As well as security filter intended to end webshells.
Unit 42 scientists mentioned “the very best defence against this evolving campaign is a security posture that favours prevention”. Organizations are encouraged to patch all scenarios and assess the company need for all internet-dealing with Zoho merchandise.
Zoho prospects are also recommended to evaluate all data files that have been developed in the affected solutions due to the fact October 2021 and get in touch with Device 42 if they feel they are influenced.
IT Pro has contacted Zoho for comment on the research.
Some parts of this report are sourced from:
www.itpro.co.uk


 Twitter and Meta Tackle Anti-Vaxxers and Chinese Disinformation
Twitter and Meta Tackle Anti-Vaxxers and Chinese Disinformation